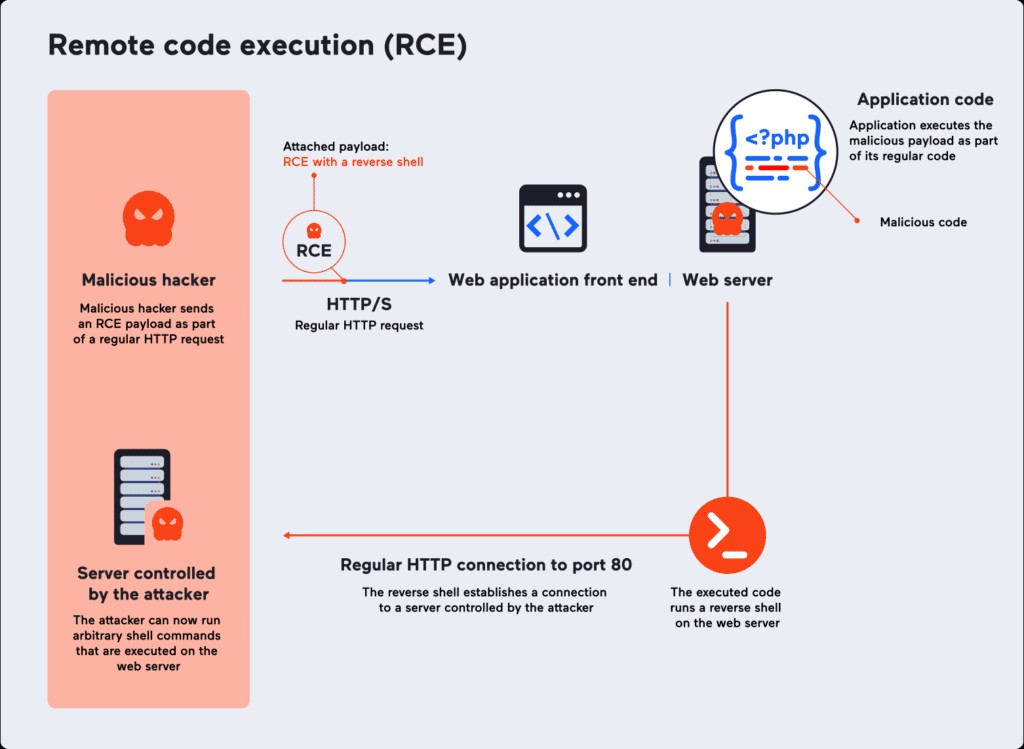
A severe security vulnerability has been discovered in Apache Parquet's Java Library, putting systems at risk of remote code execution attacks. The flaw, identified as CVE-2025-30065, received the highest possible severity rating with a CVSS score of 10.0.
Apache Parquet, an open-source columnar data file format launched in 2013, is widely used for efficient data processing and retrieval. The vulnerability affects all versions up to and including 1.15.0 and has been fixed in version 1.15.1.
The security flaw lies in the schema parsing component of the parquet-avro module. Attackers can exploit this vulnerability by crafting malicious Parquet files that, when read by vulnerable systems, enable arbitrary code execution. Data pipelines and analytics systems that process Parquet files from external or untrusted sources are particularly at risk.
While no active exploits have been reported, security experts warn that Apache project vulnerabilities are frequently targeted by threat actors. A recent example involves Apache Tomcat, where attackers began exploiting a critical flaw within 30 hours of its disclosure.
The discovery was credited to Keyi Li of Amazon. Organizations using Apache Parquet are strongly advised to upgrade to version 1.15.1 immediately to protect their systems from potential attacks.
This vulnerability emerges amid increasing concerns about the security of open-source components in enterprise systems. Recent incidents have shown how quickly attackers can weaponize such vulnerabilities, making prompt patching and security updates critical for maintaining system integrity.