A sophisticated new phishing campaign that exploits corrupted files to bypass security measures has emerged, according to cybersecurity researchers at ANY.RUN. The attack, detected since August 2024, uses deliberately damaged Microsoft Office documents and ZIP archives to slip past antivirus software and email filters.
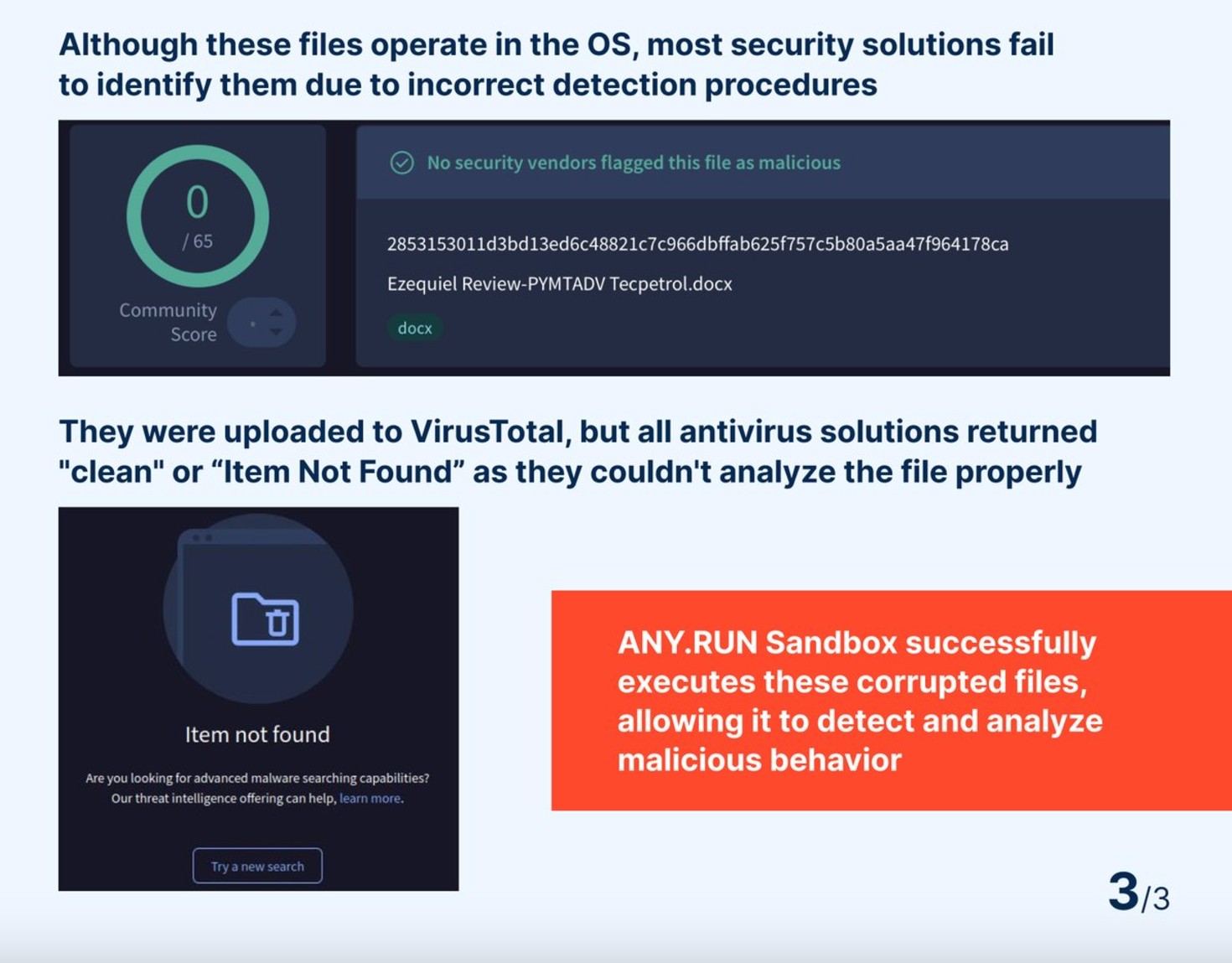
The hackers send phishing emails containing corrupted file attachments that appear to be about employee benefits or bonuses. While these files cannot be properly scanned by security tools due to their damaged state, they remain functional thanks to built-in recovery features in common programs like Microsoft Word, Outlook, and WinRAR.
When users attempt to open these corrupted files, the applications prompt them to recover the contents. If approved, the recovery process reconstructs the malicious files, potentially exposing users to embedded QR codes. These codes redirect victims to fraudulent websites designed to steal credentials or deploy malware.
"The file remains undetectable by security tools, yet user applications handle it seamlessly due to built-in recovery mechanisms exploited by attackers," explained ANY.RUN researchers.
The technique works because security solutions fail to properly examine the corrupted archives. When antivirus software attempts to scan these files, it cannot extract the contents and subsequently skips the scanning process entirely. This allows the malicious files to reach users' inboxes undetected.
This new attack method demonstrates how cybercriminals continue developing innovative ways to circumvent email security. Organizations are advised to strengthen their email filtering systems and train employees to be cautious when handling unexpected attachments, especially those requiring file recovery.
Users should verify the legitimacy of emails containing attachments, particularly those making enticing offers about compensation or benefits. Extra scrutiny should be applied to files that appear damaged or require recovery steps to open.