North Korean hacking group Lazarus has developed a sophisticated new technique to hide malicious code on Apple computers by exploiting macOS extended attributes, according to cybersecurity researchers at Group-IB.
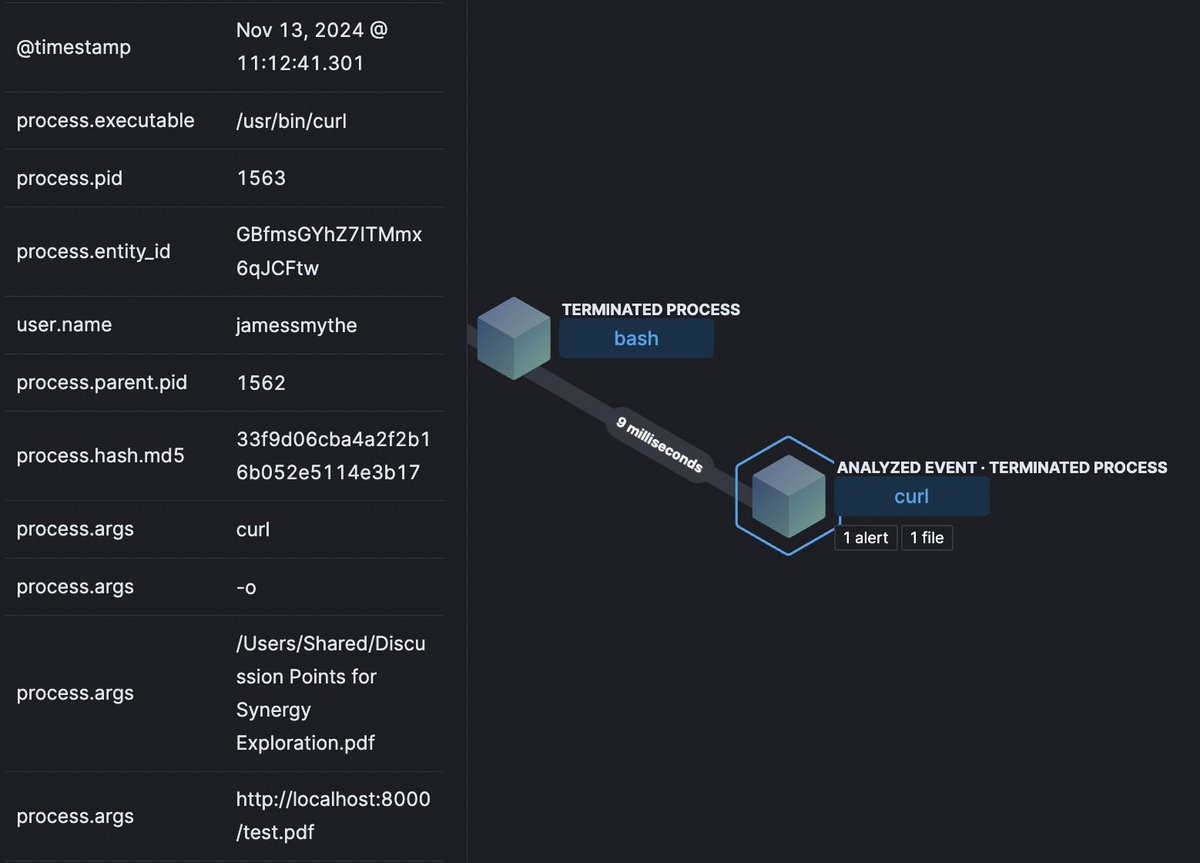
The advanced persistent threat (APT) group created a new malware called "RustyAttr" that cleverly conceals itself within the metadata typically used to store additional file information on macOS systems. This novel approach allows the malware to bypass standard security detections.
Built using the Tauri framework, which combines web frontend elements with a Rust backend, RustyAttr can operate stealthily on targeted Mac computers. The malware executes through Tauri's built-in commands while remaining hidden in extended attributes, making it completely undetectable by common antivirus tools.
To further mask their activities, the attackers employ deceptive tactics including fake system messages and decoy PDF documents about cryptocurrency and project development. While users are distracted by these elements, the malware quietly connects to Lazarus-controlled servers to download additional malicious code.
The researchers noted connections between this campaign and previous Lazarus operations, including references to their 2023 RustBucket malware. While Group-IB expressed moderate confidence in attributing these attacks to Lazarus, they have not yet identified specific victims.
Apple's built-in Gatekeeper security prevents unauthorized applications from running by default. However, users who override these protections could potentially expose their systems to this threat. Security experts recommend maintaining strict Gatekeeper settings and avoiding downloads from unknown sources.
This innovative code smuggling technique represents a concerning evolution in macOS malware development, as it has not yet been documented in standard threat frameworks. The discovery highlights the ongoing cat-and-mouse game between cybersecurity defenses and increasingly sophisticated attack methods.