A new ransomware variant called Helldown is actively targeting organizations by exploiting vulnerabilities in Zyxel firewall VPN systems, according to recent security research findings.
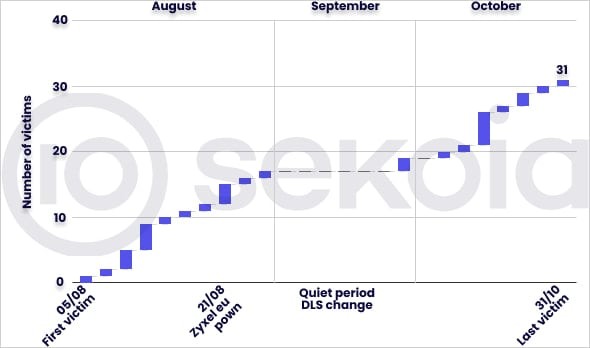
The ransomware group, which emerged in August, has already claimed 31 victims across multiple sectors including transportation, manufacturing, healthcare, telecommunications, and IT services. Most targets have been small and medium-sized businesses in the United States.
Security researchers at Sekoia report that the attackers are leveraging both known and undocumented vulnerabilities in Zyxel firewalls running firmware version 5.38. Once they gain access, the threat actors create temporary VPN accounts to further infiltrate victim networks.
"While the ransomware code itself is fairly standard, what makes this group dangerous is their access to and effective use of undocumented vulnerability exploits," notes Jeremy Scion, a researcher at Sekoia.
The group has demonstrated sophisticated initial compromise techniques, using legitimate tools and "living-off-the-land" tactics after breaching networks. Their arsenal includes common remote access tools like TeamViewer and Windows RDP for movement within networks.
A concerning aspect of Helldown's operations is their aggressive data theft approach. The group steals unusually large volumes of data, with some stolen file archives reaching 431GB. They then threaten to publish this data unless ransoms are paid.
The ransomware now includes both Windows and Linux variants, with the Linux version specifically targeting VMware ESXi servers. This expansion shows the group's intent to disrupt virtualized infrastructure that many businesses rely on.
Security experts advise organizations using Zyxel firewalls to apply all available security updates, monitor for suspicious activity, and maintain robust backup systems. The threat actor's ability to exploit undocumented vulnerabilities makes preventive security measures particularly important.
Some researchers have noted similarities between Helldown and earlier ransomware strains like DarkRace and DoNex, suggesting possible connections or rebranding, though these links remain unconfirmed.