Security researchers have uncovered a sophisticated malware campaign targeting macOS users, marking the first observed instance of North Korean hackers weaponizing Google's Flutter framework for malicious purposes.
The investigation by Jamf Threat Labs revealed three distinct variants of malware, with the most notable being embedded within Flutter-based applications. Flutter, Google's cross-platform development framework, provides unique code structuring that makes malicious code detection particularly challenging.
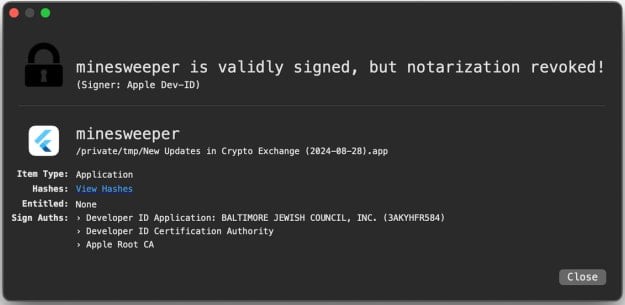
The primary malware strain was discovered in an application masquerading as a cryptocurrency exchange update, complete with a functional minesweeper game to appear legitimate. Two additional variants were built using Go and Python programming languages, demonstrating the attackers' diverse technical approach.
The malware's capabilities center around executing AppleScript commands, allowing attackers to gain remote control of infected systems. In a particularly cunning move, some malicious scripts were written in reverse to bypass security detection mechanisms.
Among the four infected applications identified, two carried developer signatures, which Apple has since revoked. One application, titled "New Updates in Crypto Exchange (2024-08-28).app," contained a modified version of an open-source iOS game.
Security experts believe this could be a test run for future attacks, specifically examining whether signed applications containing concealed malicious code could bypass Apple's notarization process and antivirus detection.
While no active attacks using these malware variants have been confirmed, the discovery highlights an emerging threat to Mac users. The targeting of cryptocurrency-related applications suggests financial motivation behind these attacks.
Mac users are advised to:
- Download applications exclusively from the Mac App Store
- Maintain current security settings
- Keep systems updated
- Exercise caution with cryptocurrency-related applications
- Be suspicious of unsolicited software offerings
The discovery underscores the evolving sophistication of North Korean cyber operations and their adoption of legitimate development tools for malicious purposes.