North Korean state-sponsored hacking group Slow Pisces has launched a sophisticated campaign targeting cryptocurrency developers through fake job recruitment efforts on LinkedIn, according to a new report from Unit 42, Palo Alto Networks' research division.
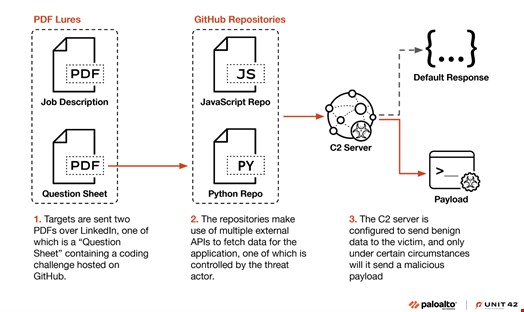
The attackers, masquerading as recruiters, approach developers with seemingly legitimate job opportunities and coding challenges. The process begins with a benign PDF containing a job description, followed by a technical assessment that directs victims to malicious GitHub repositories.
These repositories, primarily written in Python and JavaScript, appear to contain legitimate code for analyzing market data, sports statistics, and cryptocurrency prices. However, they secretly distribute two newly discovered malware variants - RN Loader and RN Stealer.
The RN Stealer malware specifically targets macOS systems, stealing sensitive information including:
- User credentials and machine details
- Application data
- SSH keys
- Cloud service configurations (AWS, Kubernetes, Google Cloud)
- Directory contents
- Saved login credentials
The group employs advanced techniques to avoid detection, including memory-only payloads and sophisticated validation methods before delivering malware. Rather than launching broad phishing campaigns, Slow Pisces carefully selects targets through LinkedIn to maintain strict control over malware distribution.
The threat actor, also known as Jade Sleet and TraderTraitor, has a track record of successful cryptocurrency heists. In 2023, they reportedly stole over $1 billion from the cryptocurrency sector. More recently, they were linked to a theft from a Japanese cryptocurrency company and an alleged $1.5 billion heist from a Dubai-based exchange.
Both GitHub and LinkedIn have removed the identified malicious accounts and repositories. However, security researchers warn that the campaign may continue through 2025, emphasizing the need for strict separation between personal and corporate devices to protect against such targeted attacks.