Cybersecurity researchers have uncovered that a sophisticated hacking group called ToddyCat successfully exploited a security flaw in ESET's antivirus software to secretly install malware on targeted systems.
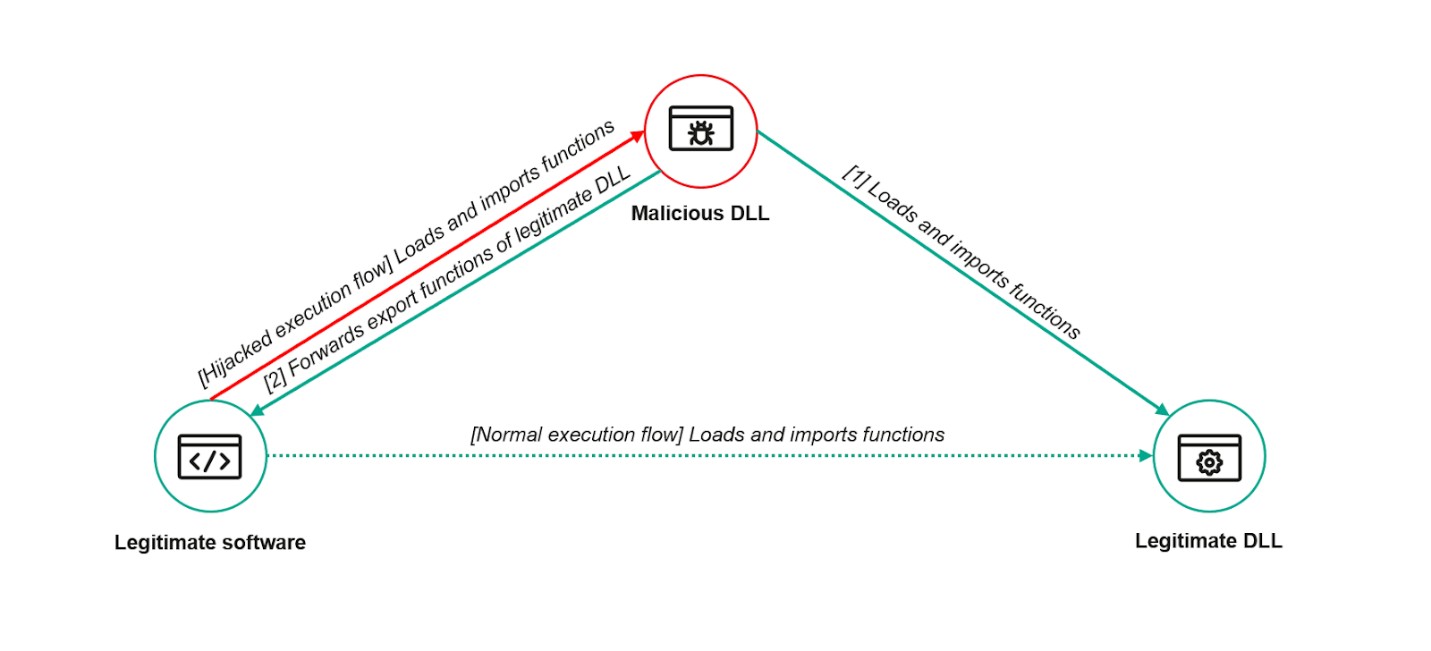
The vulnerability, identified as CVE-2024-11859, allowed attackers with administrator access to trick ESET's command-line scanner into loading malicious code instead of legitimate system files. This technique, known as DLL Search Order Hijacking, enabled the group to deploy a new malware tool called TCESB.
According to Kaspersky's analysis, TCESB is an advanced C++ tool designed to evade security monitoring by exploiting a vulnerable Dell driver. Once installed, the malware waits for encrypted payload files, decrypts them using embedded keys, and executes them directly in system memory - all while avoiding detection.
"The malware employs sophisticated techniques to maintain stealth, including detailed activity logging and support for encrypted payloads," noted Kaspersky researchers who discovered the attack campaign in early 2024.
ESET addressed the security flaw in January through a software update. The company clarified that while the vulnerability allowed code execution, it required attackers to already have administrator privileges on the targeted system.
The discovery highlights how threat actors continue finding creative ways to bypass security tools, even using them as attack vectors. Security experts recommend organizations promptly update their ESET software and monitor systems for signs of compromise.
This incident serves as a reminder that maintaining up-to-date security software and monitoring for unusual system behavior remains critical for protecting against sophisticated cyber threats.