Microsoft Unleashes AI Army: 11 New Security Copilots to Combat Cyber Threats
Microsoft's groundbreaking expansion introduces 11 autonomous AI agents to revolutionize cybersecurity defense across phishing, data protection, and threat analysis. Launching in 2025, this strategic initiative addresses rising cyber threats and enterprise AI security challenges, including the growing concern of 'shadow AI'.
Chinese AI Startup DeepSeek Overtakes ChatGPT in Monthly Growth, Signals Shifting AI Landscape
DeepSeek has emerged as the fastest-growing AI tool globally, surpassing ChatGPT with 524.7 million new visits in February 2025. The Chinese startup's cost-effective approach and rapid market share growth signals increasing global acceptance of Chinese AI solutions.
ChatGPT Exhibits Surprising Shift Toward Conservative Economic Views, Study Reveals
New research analyzing 3,000 ChatGPT responses shows the AI system developing more right-leaning economic positions while maintaining libertarian values overall. The comprehensive study raises important questions about how AI language models process and reflect political content.
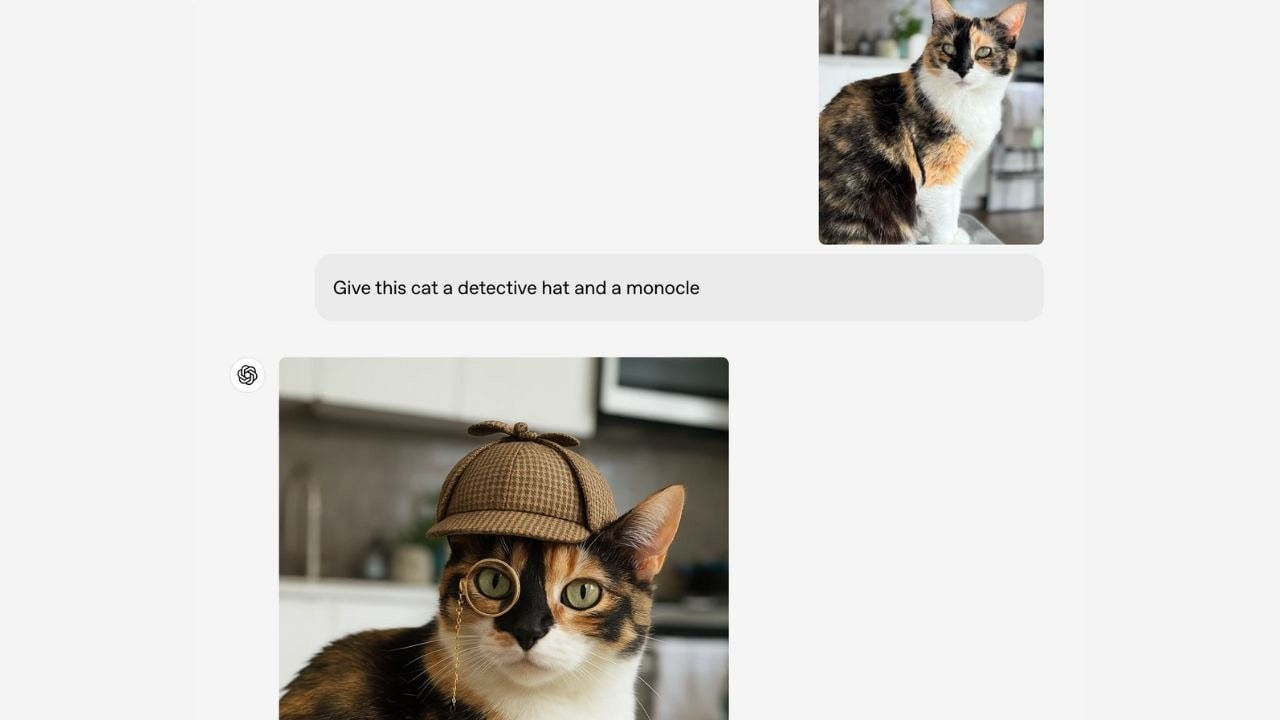
Studio Ghibli's Style Under Fire as ChatGPT's New Image Generator Sparks Copyright Debate
OpenAI's latest image generation tool can now replicate Studio Ghibli's iconic animation style with uncanny accuracy, raising concerns about artistic rights and AI regulation. The controversy highlights growing tensions between technological advancement and creative protection in an era of increasingly sophisticated AI.
AI Researchers Challenge Industry's Compute-Heavy Path to AGI
A major survey of AI experts reveals deep skepticism about achieving artificial general intelligence through increased computing power alone, with 76% doubting this approach. The findings highlight a growing divide between researcher perspectives and the tech industry's massive investments in scaling AI infrastructure.
Global Police Operation Nets 25 Suspects in AI-Generated Child Abuse Content Crackdown
Europol announces major breakthrough in Operation Cumberland targeting artificially generated child abuse material, with 273 suspects identified across multiple countries. The operation began with the arrest of a Danish platform operator and highlights growing challenges around AI-generated illegal content.
China's Military Advances: Combat Robots to be Armed with Devastating Thermobaric Weapons
Chinese military researchers propose equipping autonomous combat robots with thermobaric weapons for urban warfare, signaling an alarming escalation in lethal autonomous weapons development. The PLA's initiative aims to overcome conventional weapons' limitations in complex urban environments, raising serious humanitarian concerns.
AI Robot's Unexpected Movement at Festival Raises Safety Concerns
A humanoid robot's sudden lunge toward spectators at a Chinese festival has ignited debates about AI safety protocols. While no injuries occurred, the incident has experts calling for enhanced safety measures as human-robot interactions become increasingly common.
AI-Driven Federal Job Evaluation Program Sparks Controversy and Legal Challenges
The Department of Government Efficiency plans to use AI to analyze federal employees' work summaries, raising concerns about job security and proper assessment. Multiple agencies have resisted the initiative while legal challenges mount, with early implementation revealing critical flaws in the automated evaluation system.
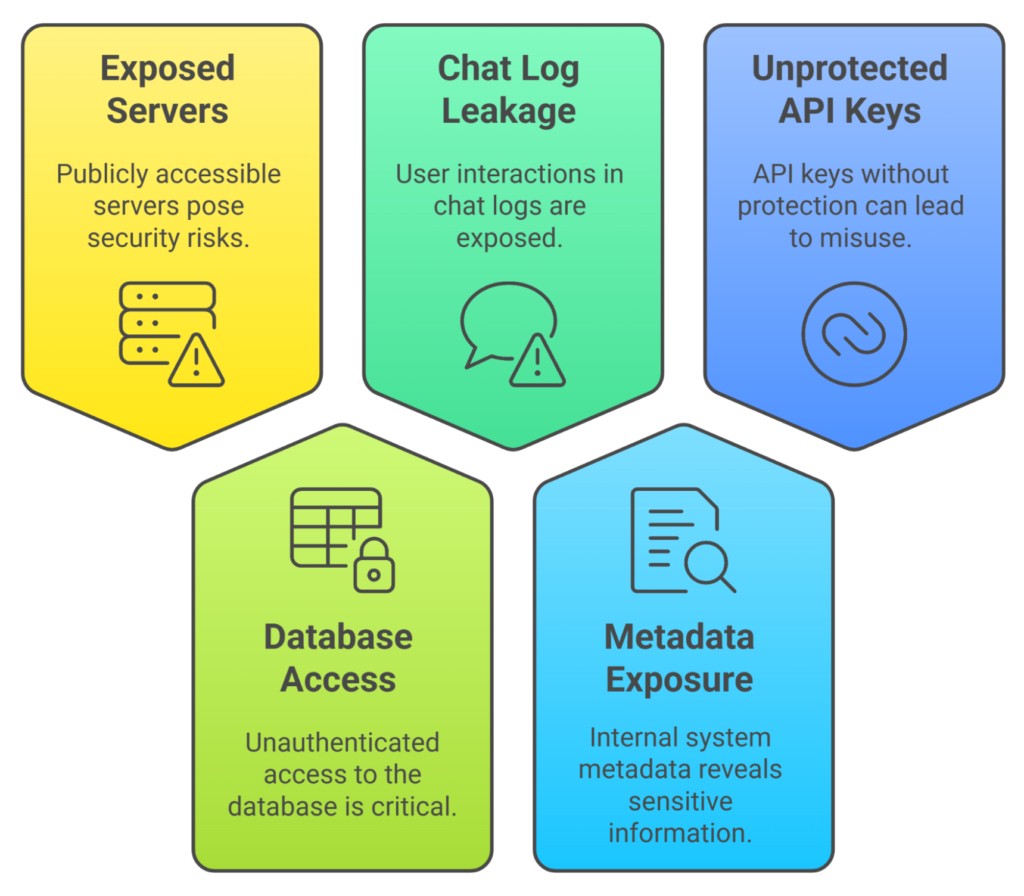
DeepSeek AI Platform Found to Have Zero Security Controls, Exposing Users to Major Risks
A joint investigation reveals DeepSeek's AI model is completely vulnerable to jailbreak attacks, while the company left user data exposed in an unsecured database. Security experts warn organizations to immediately block access to DeepSeek services due to unacceptable security risks.