CISA Faces Critical Mission Challenges Amid Workforce Reductions
Congressional officials and cybersecurity experts express grave concerns about CISA's ability to protect federal networks as the agency grapples with staffing cuts. The workforce challenges come at a critical time with over 500,000 cybersecurity positions vacant nationwide.
Chinese SMS Phishing Kit Targets U.S. Toll Road Users in Massive Fraud Operation
A sophisticated Chinese-made SMS phishing kit called Lighthouse is enabling widespread fraud targeting toll road users across eight U.S. states. The scam uses fake E-ZPass payment pages to steal financial information, with criminals deploying over 60,000 domain names to evade detection.
Critical RCE Flaw in CentreStack File Sharing Platform Actively Exploited in the Wild
A severe vulnerability in CentreStack's file-sharing platform enables attackers to execute unauthorized code through hardcoded security keys. The actively exploited flaw affects both CentreStack and Triofox enterprise solutions, with patches now available from developer Gladinet.
X Platform Hit by Major Service Disruption Affecting Thousands
X, formerly Twitter, faced widespread technical issues leaving over 53,000 users unable to access the platform. The latest outage adds to a series of challenges since Elon Musk's acquisition, highlighting ongoing stability concerns amid significant organizational changes.
Critical Vulnerabilities in mySCADA myPRO Put Industrial Control Systems at Risk
Two severe security flaws discovered in mySCADA myPRO industrial control system could allow attackers to seize control of critical infrastructure. The vulnerabilities, rated 9.3 out of 10 in severity, enable command injection attacks through inadequate input validation.
TP-Link Routers Under US Government Scrutiny: Security Concerns and Consumer Impact
US government agencies are investigating TP-Link over potential security vulnerabilities and Chinese state influence, despite the company's recent restructuring efforts. The investigation raises important questions about cybersecurity, geopolitical tensions, and consumer trust in router manufacturers.
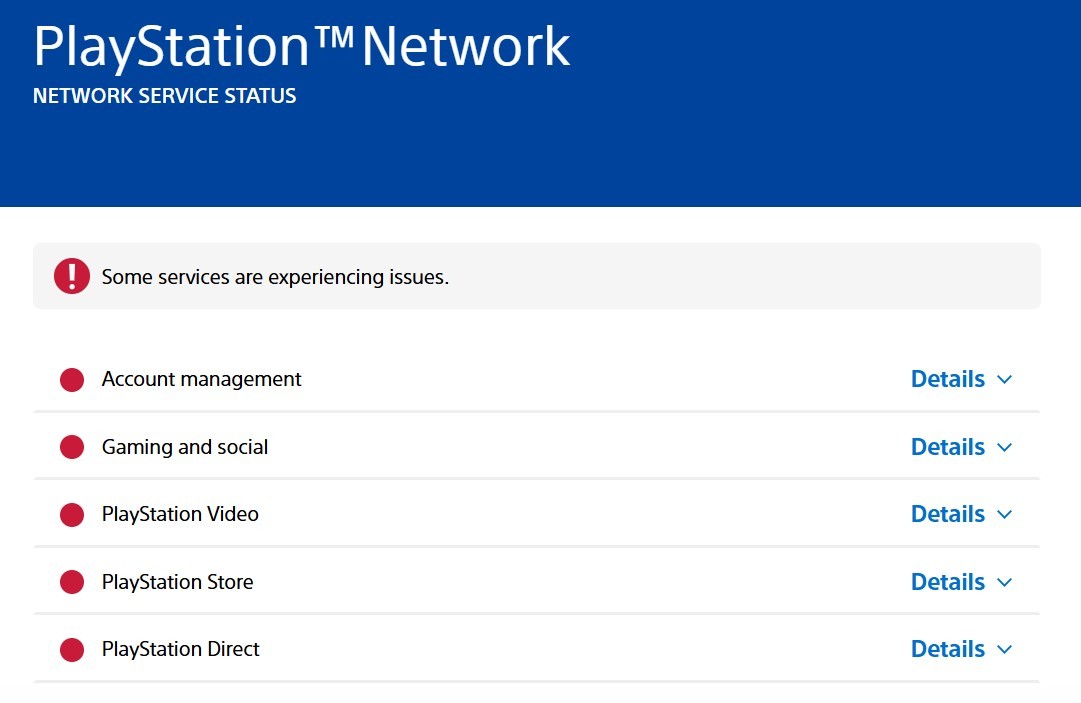
PSN's 24-Hour Outage Disrupts Gaming Services and Sparks Network Reliability Concerns
A major PlayStation Network outage left millions of players unable to access online gaming services for nearly 24 hours, impacting all platforms and core features. Sony cited an 'operational issue' and offered compensation to subscribers, while the incident raised questions about network dependability in cloud gaming.
Quantum Teleportation Breakthrough Links Processors for Distributed Computing
Oxford University researchers achieve quantum teleportation between processors 2 meters apart, enabling distributed quantum computing. The groundbreaking experiment demonstrates quantum gate operations with 70% accuracy using ion traps, marking a crucial step toward scalable quantum computers.
Abandoned AWS Storage Buckets: A Critical Supply Chain Attack Risk
Security researchers reveal how abandoned AWS S3 storage buckets can be exploited for large-scale cyberattacks, potentially enabling SolarWinds-like supply chain compromises. The study found approximately 150 deserted buckets previously used by major organizations receiving millions of file requests.
Critical Alert: J-magic Malware Targets Enterprise Networks Through Juniper Router Vulnerabilities
A sophisticated malware campaign dubbed J-magic is actively compromising corporate networks by targeting Juniper routers running JunoOS. The attacks use a custom backdoor that creates reverse shell access when triggered by magic packets, with infections detected across 36 global IP addresses.