North Korean Hackers Target Crypto Developers Through LinkedIn Job Scam
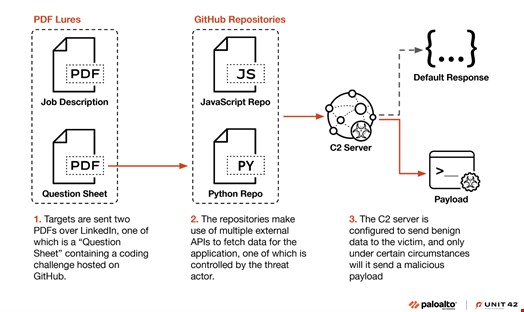
A sophisticated North Korean hacking group dubbed Slow Pisces is exploiting LinkedIn to target cryptocurrency developers with malware through fake job recruitment. The campaign has already led to major cryptocurrency heists totaling over $1 billion in 2023 alone.
Chinese State Hackers Deploy SNOWLIGHT Malware in Global Linux System Attack Campaign
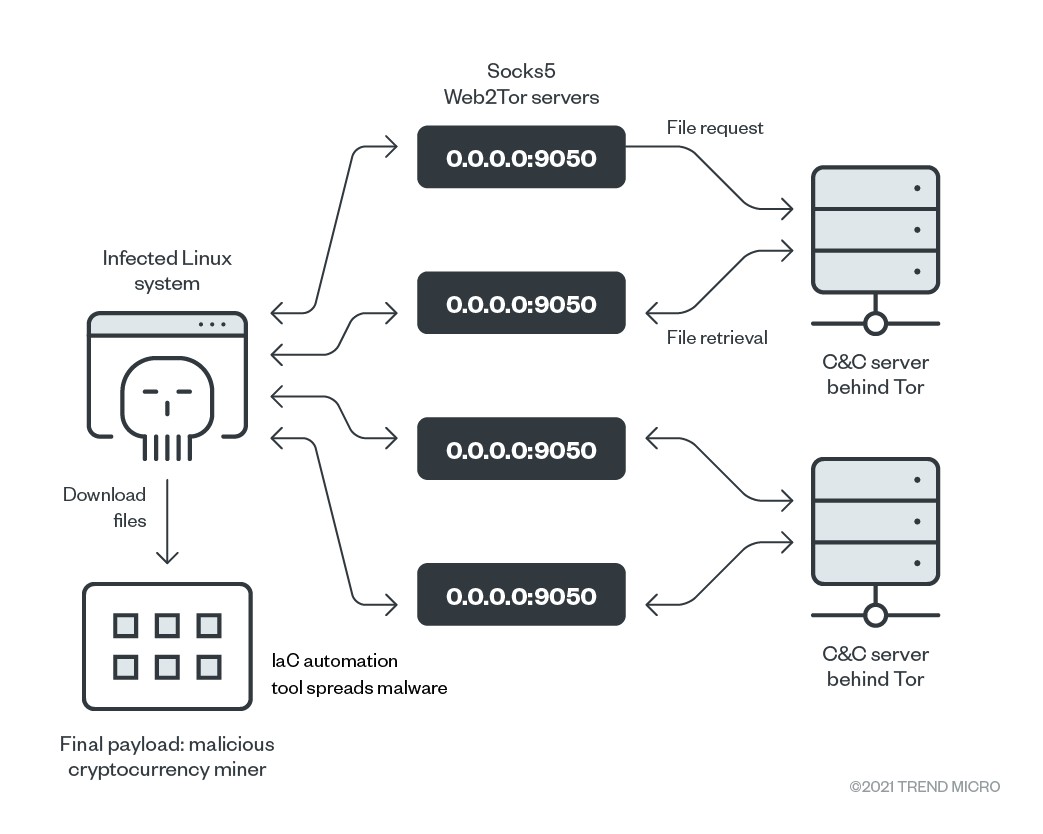
Chinese state-sponsored group UNC5174 launches sophisticated attack campaign targeting Linux systems using SNOWLIGHT malware and VShell RAT. The operation, affecting multiple sectors across 20 countries, demonstrates a strategic shift toward open-source tools to evade detection.
Healthcare Industry Targeted by Sophisticated ResolverRAT Malware Campaign
A new sophisticated malware called ResolverRAT is actively targeting pharmaceutical and healthcare organizations through multilingual phishing campaigns. The malware employs advanced in-memory execution and evasion techniques to steal sensitive data while avoiding detection.
ToddyCat Hackers Exploit ESET Antivirus Flaw to Deploy Stealthy TCESB Malware
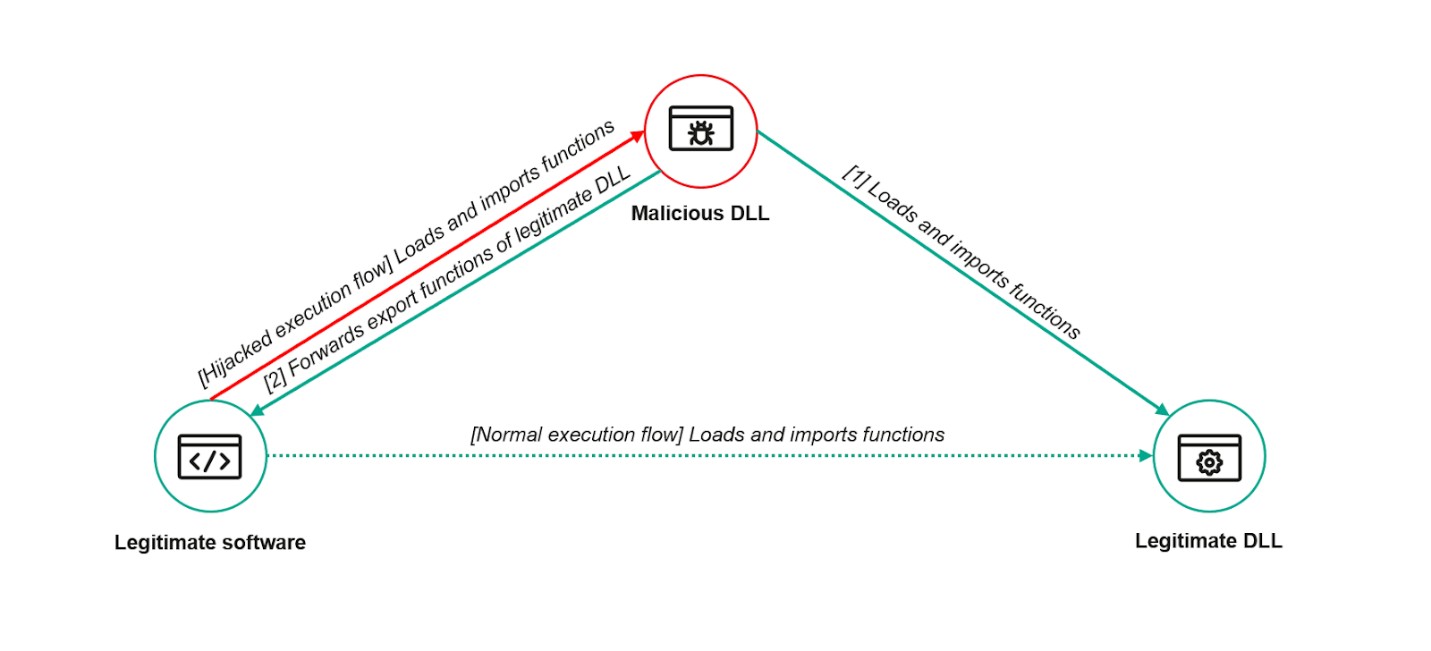
A sophisticated hacking group called ToddyCat successfully exploited a vulnerability in ESET's antivirus software to secretly install advanced malware. The attack leveraged DLL Search Order Hijacking to deploy TCESB, a stealthy C++ tool designed to evade security monitoring.
Critical WhatsApp Windows Flaw Could Let Attackers Disguise Malware as Innocent Files
A dangerous security vulnerability in WhatsApp's Windows client enables attackers to mask malware as harmless file attachments due to inconsistent MIME type handling. Meta urges users to immediately update to version 2.2450.6 or later to protect against potential malware attacks.
Critical Ivanti Zero-Day Vulnerability Exploited by Chinese State Hackers
A severe authentication bypass vulnerability in multiple Ivanti network products enables remote code execution, with active exploitation detected in the wild. Chinese state-sponsored group UNC5221 is deploying sophisticated malware to compromise systems, prompting urgent calls for immediate patching.
North Korean Hackers Deploy Malicious npm Packages in Sophisticated Developer-Targeting Campaign
Security researchers have discovered North Korean hackers distributing malware through 11 malicious npm packages that were downloaded over 5,600 times. The sophisticated campaign, known as 'Contagious Interview', uses fake job interviews and social engineering to target developers and infiltrate systems.
Critical WinRAR Vulnerability Evades Windows Security Protections
A newly discovered WinRAR security flaw allows attackers to bypass Windows' Mark of the Web security feature, potentially exposing users to malware. Microsoft has patched the high-severity vulnerability, which was being exploited through fake WinRAR websites distributing malicious software.
Massive Cryptocurrency Mining Operation Hijacks Over 1,500 PostgreSQL Servers
A sophisticated cyberattack campaign has compromised more than 1,500 PostgreSQL database servers for illicit cryptocurrency mining. The fileless attack, attributed to threat actor JINX-0126, employs advanced evasion techniques and targets internet-exposed instances with weak security.
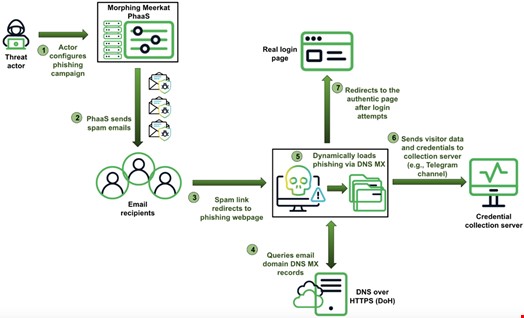
Advanced Phishing Platform 'Morphing Meerkat' Impersonates Over 100 Brands
A sophisticated phishing-as-a-service platform has emerged that can automatically generate convincing fake login pages by analyzing email domains. The threat actor's system, nicknamed 'Morphing Meerkat', uses DNS records and advanced evasion tactics to customize attacks across multiple languages.