OpenAI's GPT-5 Development Faces Major Setbacks and Uncertain Future
OpenAI's ambitious GPT-5 project is experiencing significant delays and technical challenges, falling months behind schedule despite massive investments. The setbacks highlight data limitations and raise questions about the feasibility of achieving planned AI advancement goals.
US Government Considers National Ban on TP-Link Routers Over Chinese Security Risks
Federal agencies are investigating Chinese-made TP-Link routers for potential national security threats after Microsoft revealed government-backed hackers had compromised the devices. The proposed ban, which could take effect next year, reflects growing US-China tensions over technology and security concerns.
AI Models Show Diverse Patterns in Social Cooperation Experiments
Research examining how AI agents develop social norms reveals varying abilities to foster cooperative behavior across different language models. Claude 3.5 Sonnet demonstrated superior cooperation, while other models showed mixed results in experiments testing indirect reciprocity and punishment mechanisms.
Microsoft Teams Calls Exploited in Sophisticated DarkGate Malware Campaign
Cybercriminals are leveraging Microsoft Teams and AnyDesk in a complex social engineering attack to distribute DarkGate malware. The campaign combines email phishing, vishing through Teams calls, and remote access tools to compromise systems and steal sensitive data.
Russian Hackers Hijack Criminal Networks to Target Ukrainian Starlink Devices
Russian state-backed group Secret Blizzard has adopted an unusual tactic of compromising other cybercrime groups' infrastructure to infiltrate Ukrainian military Starlink connections. Microsoft's report reveals the hackers leveraged malware tools from multiple threat actors to gather intelligence on military hardware.
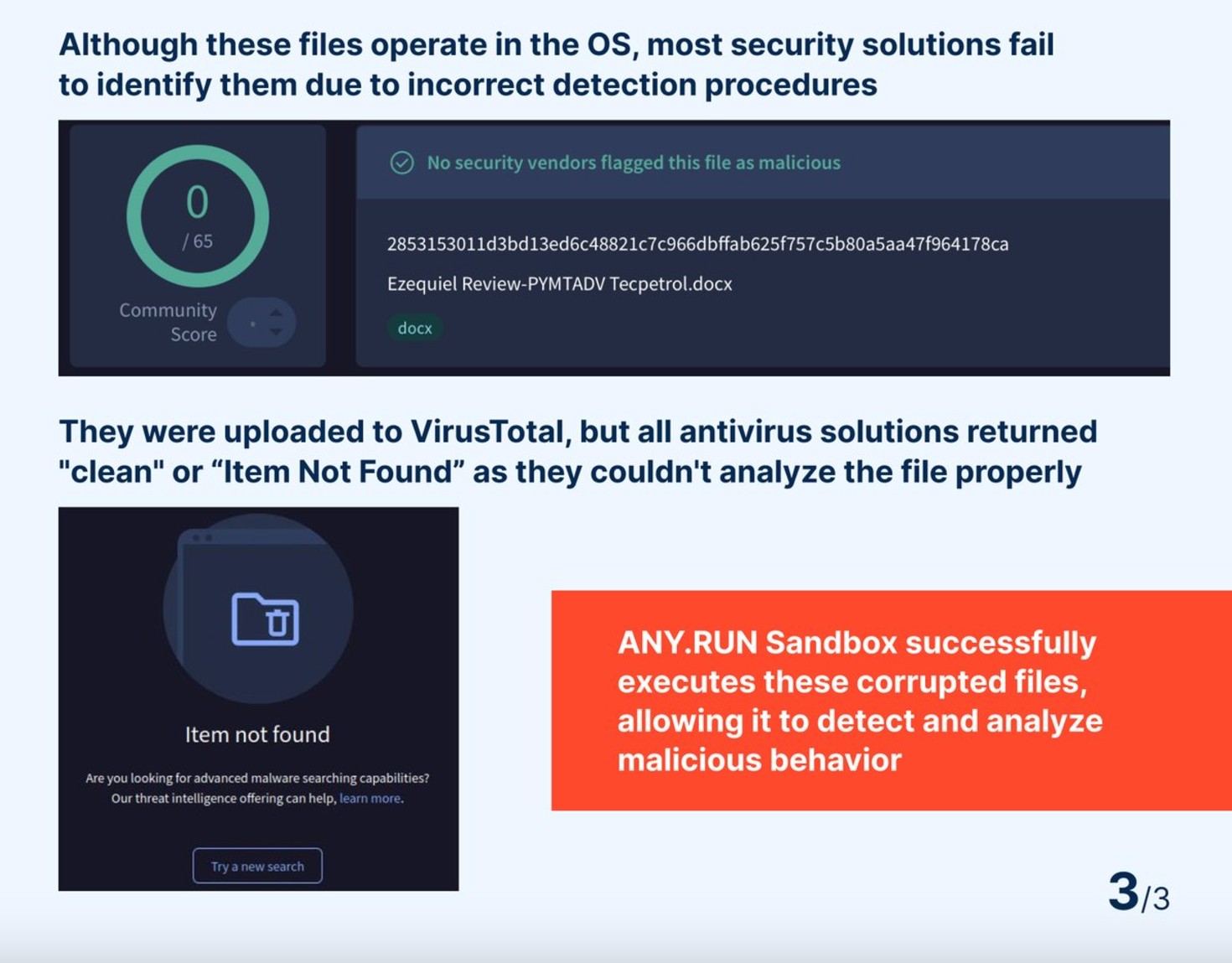
Cybercriminals Exploit Corrupted Files to Bypass Security in Sophisticated Phishing Campaign
A new phishing campaign discovered by ANY.RUN researchers uses deliberately damaged Office documents and ZIP files to evade antivirus detection. The attack leverages built-in file recovery features to deliver malicious QR codes while remaining undetectable to security tools.
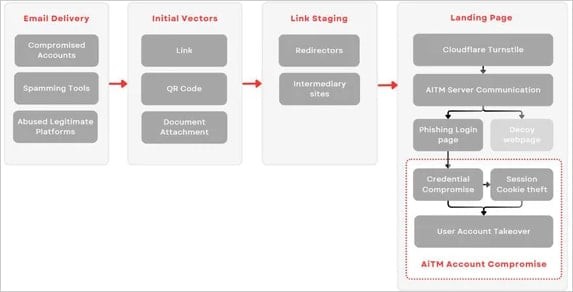
Rockstar 2FA: The New Phishing Toolkit Bypassing Microsoft 365 Security
A sophisticated phishing toolkit called Rockstar 2FA is enabling cybercriminals to bypass Microsoft 365's multi-factor authentication through adversary-in-the-middle attacks. Available for just $200, this accessible platform provides advanced features like cookie harvesting and customizable login pages that pose a significant threat to organizations.
IETF Introduces 'Do-Not-Stab' Web Standard for User Autonomy
The Internet Engineering Task Force has published RFC 35140, introducing a new HTTP header that allows users to opt out of virtual stabbings from websites. The standard addresses the growing 'Stabbings as a Service' industry while highlighting ongoing debates about user autonomy in digital spaces.
Microsoft Takes Down Global Phishing Network in Major Cybersecurity Operation
Microsoft's Digital Crimes Unit has dismantled a sophisticated Egyptian-run phishing operation that sold criminal toolkits targeting financial institutions. The takedown of over 240 websites comes as Microsoft reports a 146% increase in advanced phishing attacks, highlighting escalating efforts to combat cybercrime.
Bitdefender Releases Free Tool to Counter New ShrinkLocker Ransomware Threat
Cybersecurity firm Bitdefender has discovered ShrinkLocker, a new ransomware exploiting Windows BitLocker encryption to lock users out of their systems. In response, they've released a free decryption tool to help victims recover data without paying ransom, dealing a significant blow to cybercriminals.