Critical Gmail Security Alert: Sophisticated Phishing Scam Targets 1.8B Users
Google issues urgent warning about an advanced phishing attack exploiting official infrastructure to target Gmail's 1.8 billion users. The deceptive campaign uses authentic-looking emails from Google domains to harvest login credentials through fake legal subpoenas.
Chinese SMS Phishing Kit Targets U.S. Toll Road Users in Massive Fraud Operation
A sophisticated Chinese-made SMS phishing kit called Lighthouse is enabling widespread fraud targeting toll road users across eight U.S. states. The scam uses fake E-ZPass payment pages to steal financial information, with criminals deploying over 60,000 domain names to evade detection.
Healthcare Industry Targeted by Sophisticated ResolverRAT Malware Campaign
A new sophisticated malware called ResolverRAT is actively targeting pharmaceutical and healthcare organizations through multilingual phishing campaigns. The malware employs advanced in-memory execution and evasion techniques to steal sensitive data while avoiding detection.
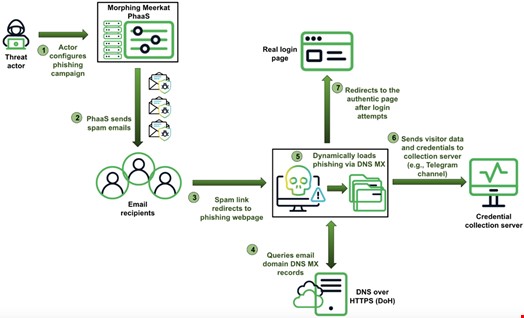
Advanced Phishing Platform 'Morphing Meerkat' Impersonates Over 100 Brands
A sophisticated phishing-as-a-service platform has emerged that can automatically generate convincing fake login pages by analyzing email domains. The threat actor's system, nicknamed 'Morphing Meerkat', uses DNS records and advanced evasion tactics to customize attacks across multiple languages.
Security Expert Troy Hunt Falls Victim to Sophisticated Mailchimp Phishing Scam
Renowned cybersecurity expert Troy Hunt became victim to a phishing attack targeting his Mailchimp newsletter service, exposing 16,000 subscriber records. His transparent response and swift action in addressing the breach sets an example for responsible incident disclosure.
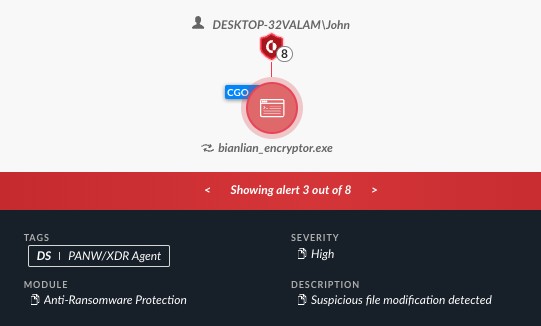
Scammers Impersonate BianLian Ransomware Group in Mail-Based Extortion Scheme
A sophisticated scam operation is targeting executives with fake ransomware demands delivered via physical mail, impersonating the notorious BianLian group. The fraudulent letters demand large Bitcoin ransoms while displaying key inconsistencies that reveal their opportunistic nature.
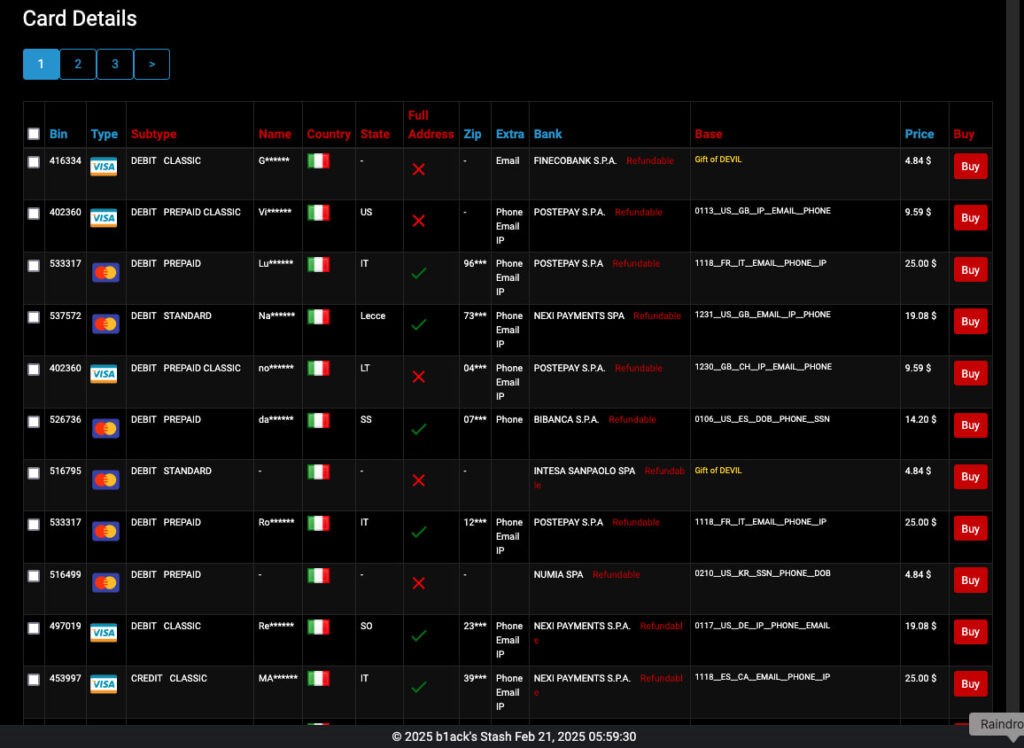
Dark Web Marketplace Releases 1 Million Stolen Credit Cards in Mass Data Breach
B1ack's Stash marketplace has leaked over 1 million stolen credit card records on the dark web, including detailed personal information of cardholders. The massive data dump appears to be a marketing tactic to attract users to their criminal enterprise platform.
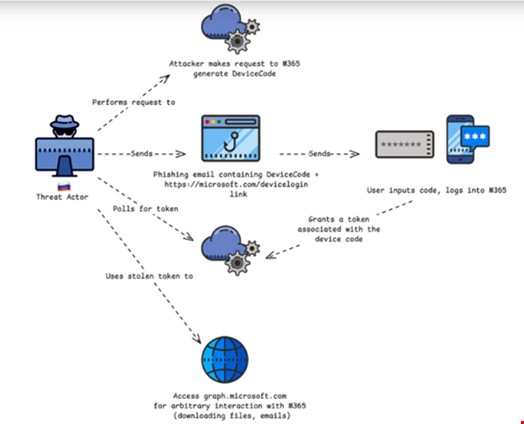
Russian Hackers Target Microsoft 365 Using Device Code Authentication Scam
Russian threat actors have launched a sophisticated phishing campaign exploiting Microsoft's device code authentication to compromise Microsoft 365 accounts across government and private sectors. The attacks, conducted by multiple groups including APT29, use social engineering tactics to bypass security measures and gain unauthorized access.
North Korean Hackers Deploy Deceptive 'ClickFix' Social Engineering Tactic
Kimsuky, a sophisticated North Korean hacking group, has been observed using a new social engineering technique called 'ClickFix' to target South Korean users. The attackers trick victims into running malicious PowerShell scripts through fake browser notifications and spear-phishing campaigns.
FBI Issues Urgent Warning About Nationwide Toll Payment Text Scam
The FBI warns iPhone and Android users about a sophisticated phishing scam involving fake toll payment texts linked to Chinese criminal groups. Users are urged to delete suspicious messages immediately as the scam has already affected thousands across multiple states.