Microsoft Teams Exploited in Sophisticated Ransomware Phishing Scams
Cybersecurity firm Sophos reveals how ransomware groups are masquerading as IT support staff in Microsoft Teams to infiltrate organizations and deploy malware. The attackers exploit Teams' default settings to initiate contact and convince employees to grant remote access control.
PayPal Users Targeted by Sophisticated Microsoft 365-Based Phishing Scam
A newly discovered phishing campaign exploits legitimate PayPal infrastructure and Microsoft 365 to hijack user accounts. The sophisticated attack bypasses traditional security by using authentic payment request notifications and URLs, making detection particularly challenging.
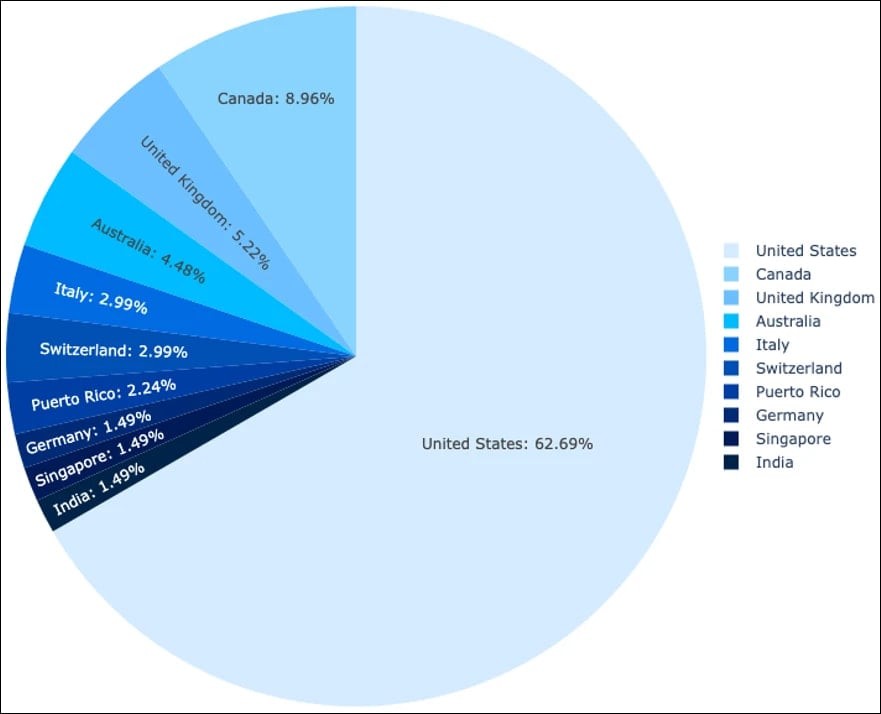
Cybercrime Evolution: FlowerStorm Rises as Rockstar2FA Phishing Platform Collapses
The sudden technical failure of Rockstar2FA phishing toolkit has paved the way for FlowerStorm, a sophisticated phishing-as-a-service platform targeting Microsoft 365 credentials. This transition highlights the resilient nature of cybercrime operations, particularly affecting service industries in developed nations.
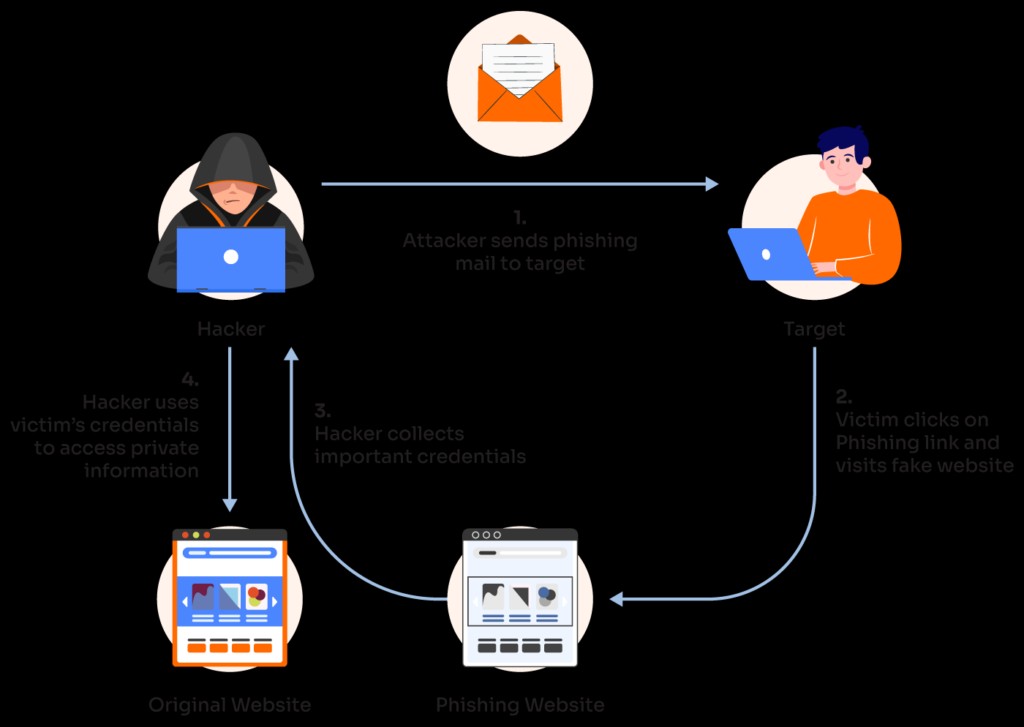
Microsoft Teams Calls Exploited in Sophisticated DarkGate Malware Campaign
Cybercriminals are leveraging Microsoft Teams and AnyDesk in a complex social engineering attack to distribute DarkGate malware. The campaign combines email phishing, vishing through Teams calls, and remote access tools to compromise systems and steal sensitive data.
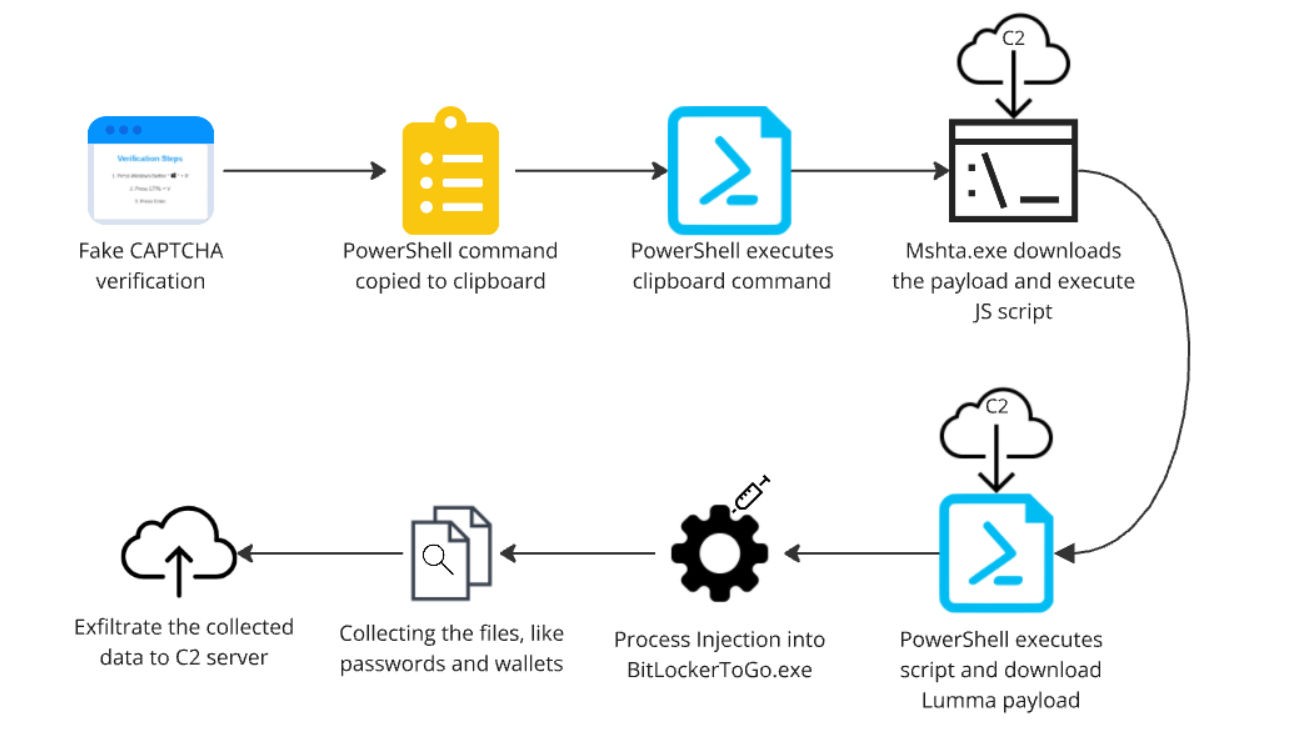
Massive Malvertising Campaign Spreads Lumma Malware Through Fake CAPTCHA Scam
Cybercriminals have launched a sophisticated attack reaching millions of users through compromised ad networks, using fake CAPTCHA verification pages to distribute the Lumma information stealer. The campaign generates over 1 million daily ad impressions across 3,000+ websites, targeting sensitive data like banking credentials and personal files.
AI Granny Bot Outsmarts Phone Scammers with Tales of Her Cat
British telecom O2 deploys Daisy, an AI system posing as a chatty grandmother, to waste scammers' time with endless stories and circular conversations. Working with scam-hunter Jim Browning, the initiative aims to disrupt fraudsters while raising awareness about telephone scams.
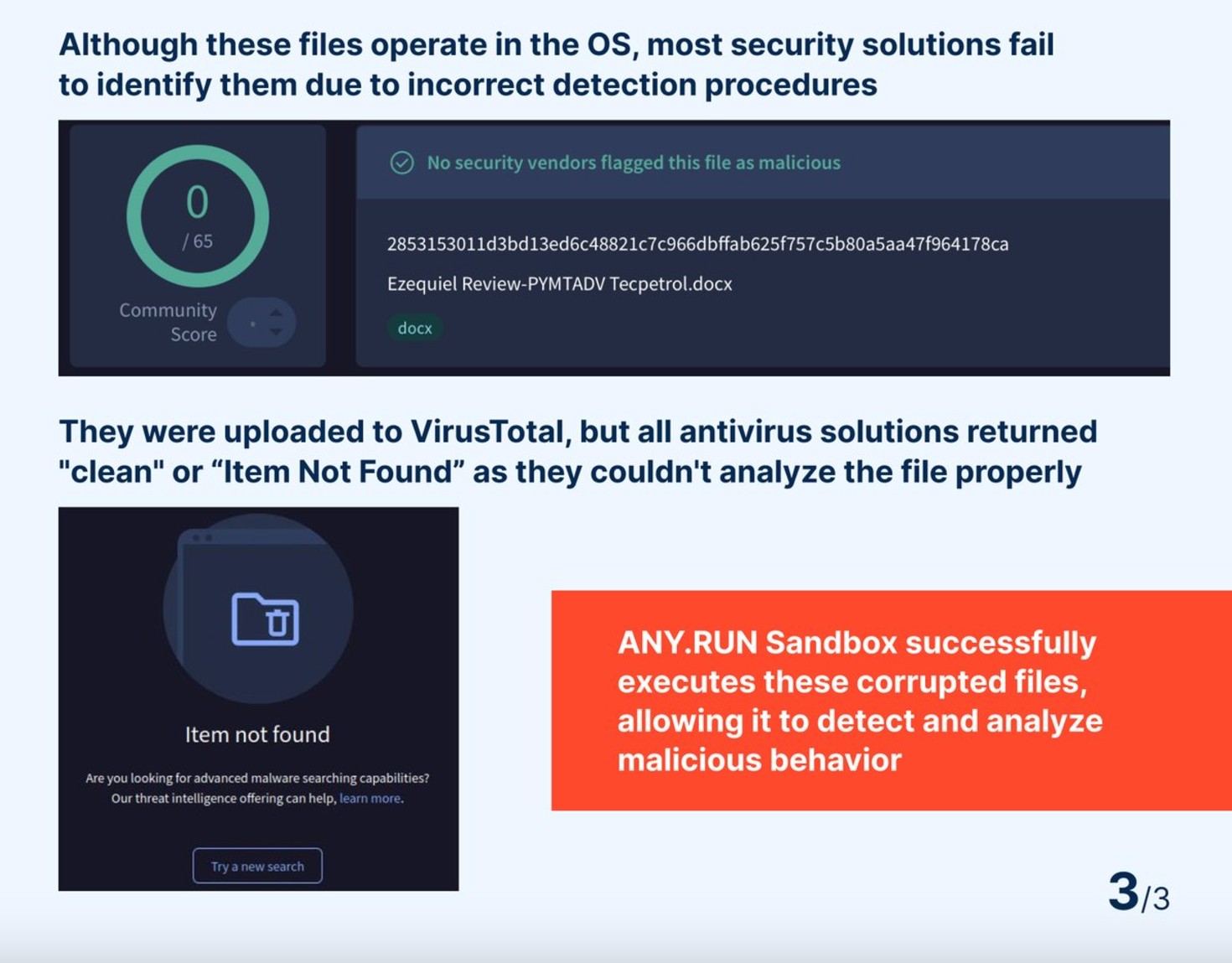
Cybercriminals Exploit Corrupted Files to Bypass Security in Sophisticated Phishing Campaign
A new phishing campaign discovered by ANY.RUN researchers uses deliberately damaged Office documents and ZIP files to evade antivirus detection. The attack leverages built-in file recovery features to deliver malicious QR codes while remaining undetectable to security tools.
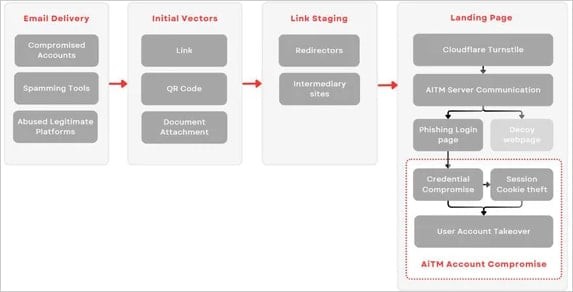
Rockstar 2FA: The New Phishing Toolkit Bypassing Microsoft 365 Security
A sophisticated phishing toolkit called Rockstar 2FA is enabling cybercriminals to bypass Microsoft 365's multi-factor authentication through adversary-in-the-middle attacks. Available for just $200, this accessible platform provides advanced features like cookie harvesting and customizable login pages that pose a significant threat to organizations.
Microsoft Takes Down Global Phishing Network in Major Cybersecurity Operation
Microsoft's Digital Crimes Unit has dismantled a sophisticated Egyptian-run phishing operation that sold criminal toolkits targeting financial institutions. The takedown of over 240 websites comes as Microsoft reports a 146% increase in advanced phishing attacks, highlighting escalating efforts to combat cybercrime.
Malicious GitHub Commits Target Security Researcher in Identity Fraud Attack
Multiple open-source projects on GitHub were compromised by unauthorized code commits falsely attributed to security researcher Stephen Lacy. The attack exploited commit verification weaknesses to damage the researcher's reputation, prompting GitHub to investigate and the community to implement stricter authentication measures.