Cybercriminals Exploit Corrupted Files to Bypass Security in Sophisticated Phishing Campaign
• 1 min read
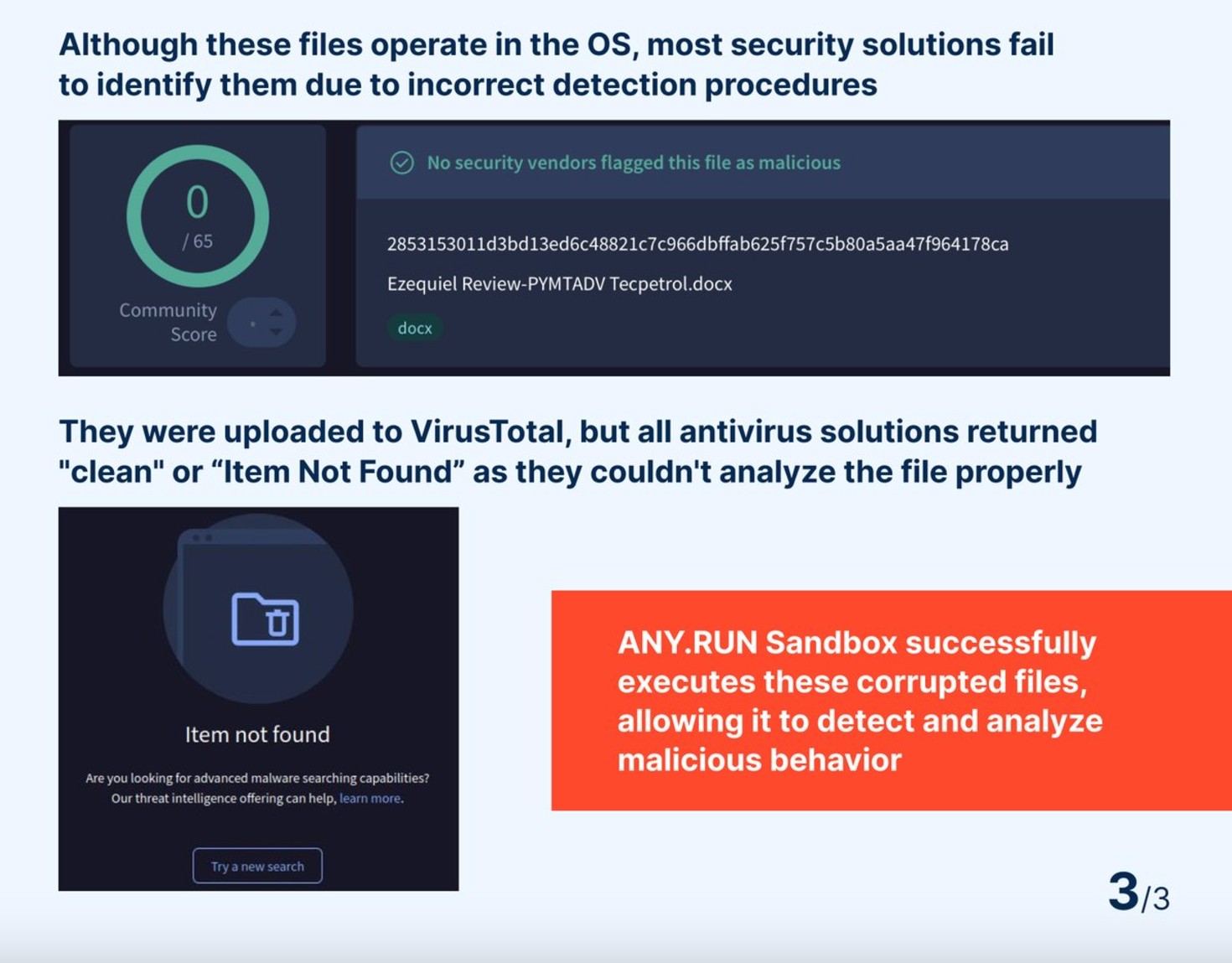
A new phishing campaign discovered by ANY.RUN researchers uses deliberately damaged Office documents and ZIP files to evade antivirus detection. The attack leverages built-in file recovery features to deliver malicious QR codes while remaining undetectable to security tools.
ZIP File Concatenation: The New Hacker Trick Bypassing Security Defenses
• 1 min read
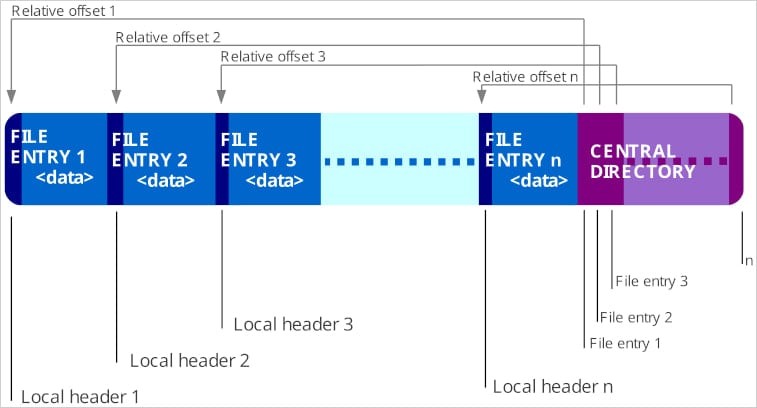
Cybercriminals are exploiting ZIP file concatenation to hide malicious payloads from security scans. This emerging tactic allows hackers to bypass traditional detection methods, posing new challenges for organizations' cybersecurity measures.