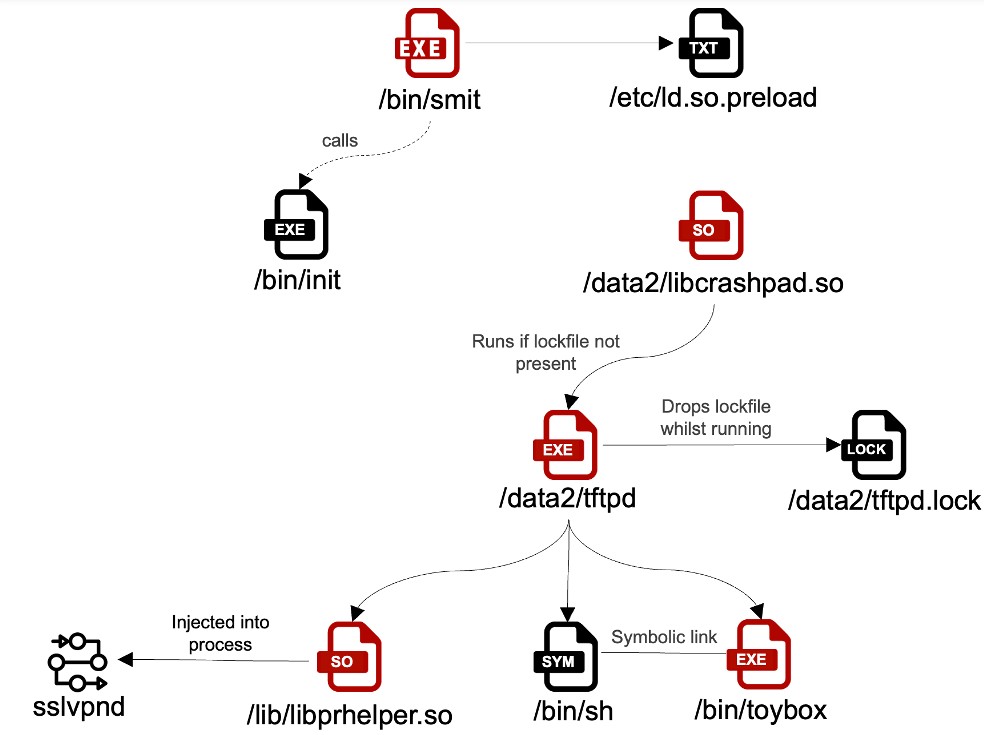
A sophisticated threat actor has been targeting FortiGate devices using a combination of known vulnerabilities and an innovative persistence method that maintains access even after security patches are applied, according to Fortinet's recent disclosure.
The attackers leveraged multiple FortiOS vulnerabilities, including CVE-2022-42475, CVE-2023-27997, and CVE-2024-21762, to initially breach the devices. However, what makes this campaign particularly concerning is their use of a symbolic link trick that allows them to retain read-only access to compromised systems even after the original vulnerabilities are patched.
"The attackers created a symbolic link between the user filesystem and root filesystem in an SSL-VPN language files folder," explained Fortinet CISO Carl Windsor. "This modification remained undetected since it occurred in the user filesystem, potentially giving attackers continued access to device configurations even after security updates."
In response, Fortinet has released updated versions of FortiOS (7.6.2, 7.4.7, 7.2.11, 7.0.17, and 6.4.16) that automatically remove the malicious symbolic link and prevent similar exploits through the SSL-VPN interface.
The company has begun notifying affected customers, recommending immediate updates to the latest FortiOS versions and thorough security reviews of potentially compromised devices. This includes resetting user credentials, revoking certificates, and updating security secrets.
International cybersecurity agencies have also raised alarms. The German Federal Office for Information Security reports nearly 700 FortiGate devices in Germany remain vulnerable to recent exploits. Meanwhile, France's CERT-FR has documented numerous compromises since early 2023 as part of a massive campaign targeting devices in their region.
The situation highlights the evolving sophistication of cyber threats, as attackers develop new methods to maintain long-term access to compromised systems. Organizations using FortiGate devices are strongly advised to implement the recommended security measures and conduct thorough system audits to detect potential compromises.