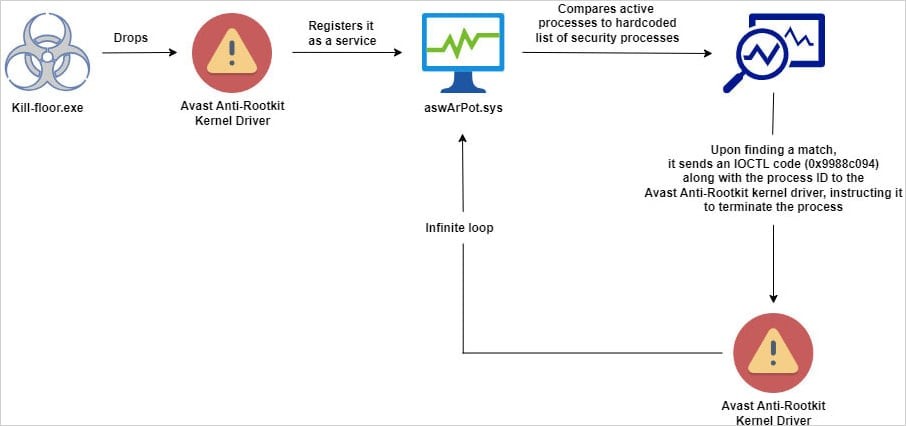
Recent reports reveal that cybercriminals have found a way to exploit Avast's anti-rootkit driver to bypass security protections on Windows systems. The driver, originally designed to detect and remove deeply embedded malware, is now being weaponized for malicious purposes.
Security researchers discovered that attackers are misusing the legitimate Avast driver (aswArPot.sys) to terminate antivirus processes and security tools. By leveraging this signed kernel driver, hackers can effectively shut down defensive measures that would normally prevent their malware from operating.
The technique, known as "Bring Your Own Vulnerable Driver" (BYOVD), allows attackers to load a legitimately signed but vulnerable driver to gain elevated system privileges. Since the Avast driver is digitally signed by a trusted vendor, Windows allows it to run with kernel-level access.
Experts note that this attack method is particularly dangerous because it uses a component from a trusted security vendor to disable the very protections meant to keep systems safe. The compromised driver provides attackers with nearly unlimited access to manipulate core system functions.
Security teams recommend that organizations monitor for unauthorized loading of the Avast anti-rootkit driver, especially on systems where Avast products are not legitimately installed. Blocking the driver through Windows security features can help prevent this type of abuse.
Industry professionals advise keeping all security software updated and maintaining robust endpoint protection that can detect driver-based attacks. Users should also be cautious about granting administrative privileges that could allow malicious driver loading.
The discovery highlights an ongoing cat-and-mouse game between security vendors and cybercriminals who continue finding creative ways to bypass protective measures. As this threat evolves, both users and security companies must remain vigilant against driver-based attack techniques.