A recently discovered vulnerability in Microsoft Bookings has raised serious concerns about the security of this widely-used scheduling application. The flaw, which allows unauthorized access to user accounts and impersonation of key personnel, has sent shockwaves through the cybersecurity community.
Microsoft Bookings, a popular tool for scheduling appointments and managing customer interactions, is used by countless businesses worldwide. The newly identified security gap potentially exposes sensitive information and could lead to severe reputational damage for affected organizations.
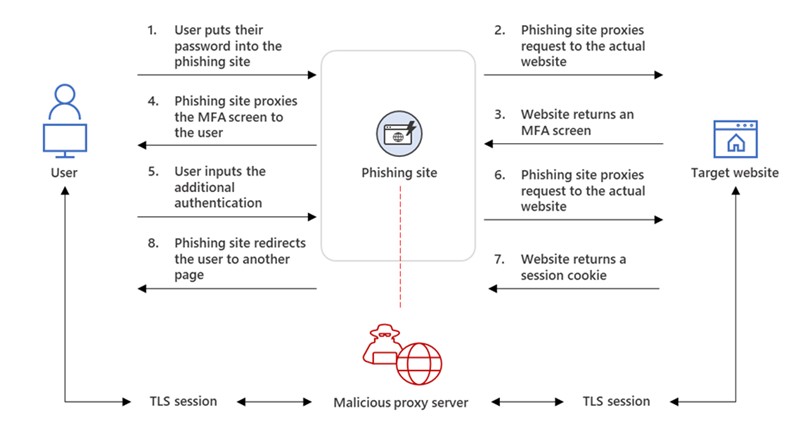
The vulnerability stems from a weakness in the authentication process of Microsoft Bookings. Attackers can exploit this flaw to gain unauthorized access to user accounts, potentially compromising confidential data and manipulating scheduling information. Even more alarming is the ability for malicious actors to impersonate key individuals within an organization, such as executives or high-level managers.
Cybersecurity experts warn that this flaw could have far-reaching consequences. An attacker could, for instance, schedule fake appointments, access sensitive customer information, or even use the compromised account to launch phishing attacks against unsuspecting clients.
Microsoft has acknowledged the issue and is working diligently to develop and deploy a fix. In the meantime, users are advised to exercise caution and implement additional security measures. These may include enabling multi-factor authentication, regularly monitoring account activity, and educating staff about potential phishing attempts.
As businesses increasingly rely on digital tools for day-to-day operations, vulnerabilities like this serve as a stark reminder of the importance of robust cybersecurity measures. Organizations using Microsoft Bookings are urged to stay vigilant and keep their systems updated with the latest security patches once they become available.
The discovery of this flaw underscores the ongoing challenges in maintaining digital security in an ever-evolving technological landscape. As cyber threats continue to grow in sophistication, both software developers and users must remain proactive in addressing potential vulnerabilities to safeguard sensitive information and maintain trust in digital platforms.