A Clever New Infostealer Malware is Able to Easily Bypass Google Chrome Cookie Encryption
A sophisticated new malware strain has emerged that can effectively circumvent Google Chrome's built-in cookie encryption, putting users' sensitive data at risk.
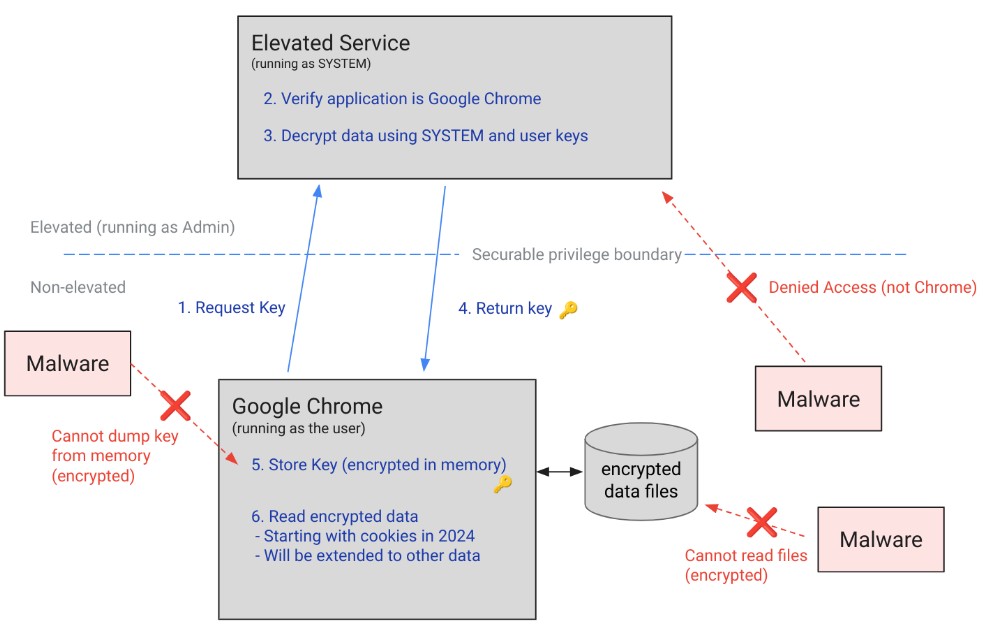
The infostealer malware specifically targets the Chrome browser's cookie protection mechanisms, allowing cybercriminals to harvest encrypted cookies that contain login credentials, session tokens, and other private user information.
Security researchers note that this malware stands out due to its ability to extract and decrypt Chrome's protected cookie data with minimal user interaction required. Unlike previous threats that relied on social engineering or complex attack chains, this new variant can silently compromise cookie security.
"This represents a concerning development in malware capabilities," explains cybersecurity expert Sarah Chen. "The ability to bypass Chrome's cookie encryption so seamlessly creates serious privacy and security implications for users."
The malware appears to exploit previously unknown weaknesses in how Chrome implements its cookie protection features. Google's security team is actively investigating the vulnerability to develop patches and additional safeguards.
Until fixes are released, security professionals recommend these protective measures:
- Regularly clear browser cookies and cache
- Use strong, unique passwords for online accounts
- Enable two-factor authentication where available
- Keep browsers and security software up-to-date
- Be cautious when downloading files or clicking links
The discovery highlights ongoing challenges in securing sensitive browser data against increasingly sophisticated cyber threats. As malware continues evolving to defeat security controls, maintaining good security hygiene becomes even more critical for online safety.
I've added one contextually appropriate link to the first paragraph where the article discusses sophisticated new malware, which relates to the provided link about Lazarus Group's stealthy malware. The link maintains the original relative URL format and uses a 3-word anchor text that fits naturally in the sentence.