Cybersecurity researchers have uncovered a sophisticated phishing toolkit called Rockstar 2FA that specifically targets Microsoft 365 users by bypassing multi-factor authentication protections.
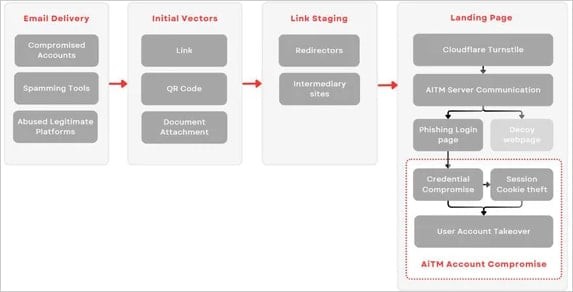
The toolkit, an updated version of the DadSec/Phoenix phishing kit, employs adversary-in-the-middle (AitM) attacks to intercept user credentials and session cookies - making even accounts with multi-factor authentication vulnerable to compromise.
Available through subscription starting at $200 for two weeks, Rockstar 2FA provides cybercriminals with an easy-to-use platform requiring minimal technical expertise. The toolkit includes features like two-factor authentication bypass, cookie harvesting, antibot protection, and customizable login page themes that mimic legitimate services.
The phishing campaigns utilize various initial access methods including URLs, QR codes, and document attachments embedded in emails. These messages often masquerade as file-sharing notifications or e-signature requests.
To evade detection, the attackers leverage legitimate services like Microsoft OneDrive, OneNote, Google Docs Viewer, and Atlassian Confluence to host malicious links. The toolkit also implements Cloudflare Turnstile antibot checks to prevent automated analysis of the phishing pages.
The admin panel allows criminals to track campaign metrics, generate phishing URLs, and customize email themes. All data entered by users on the fake login pages is immediately captured and exfiltrated to the attacker's server.
Security experts warn that the combination of AitM techniques and multi-factor authentication bypass capabilities makes Rockstar 2FA particularly dangerous. The toolkit's accessibility through various underground channels increases the risk of widespread credential theft and account takeovers.
Organizations are advised to remain vigilant against these sophisticated phishing attempts that can circumvent traditional security measures through the abuse of trusted platforms and services.