Security researchers have identified a new variant of the ZLoader malware that employs sophisticated DNS tunneling techniques to hide its command-and-control communications, marking the latest evolution of this persistent threat.
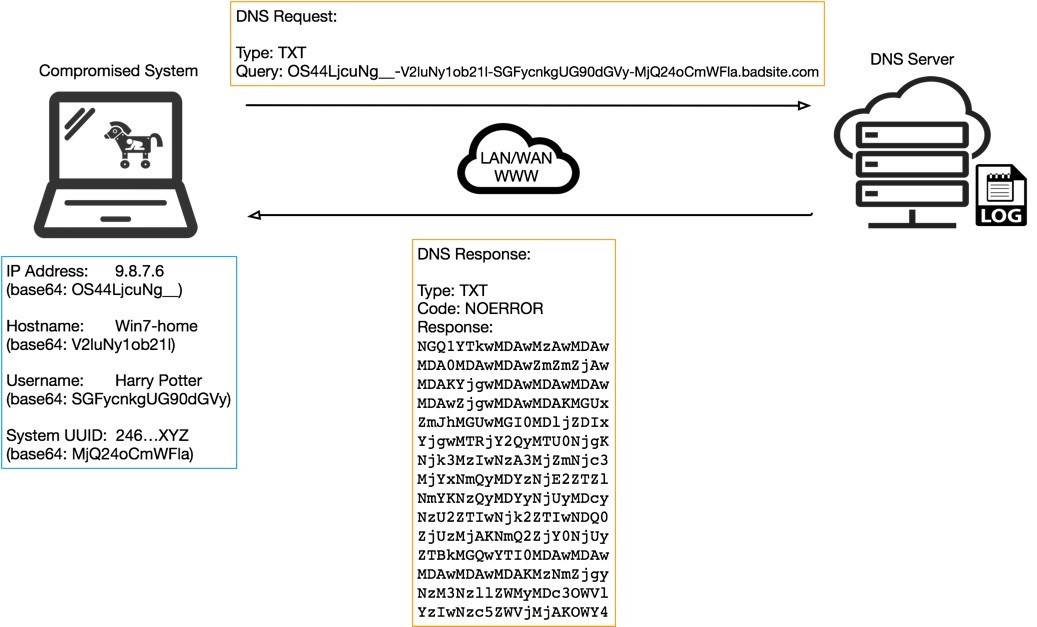
The updated version 2.9.4.0 introduces several advanced capabilities, including an interactive shell supporting multiple commands and custom DNS tunneling protocols that help the malware evade antivirus protection. These improvements make the malware more resilient against security measures.
ZLoader, also known as Terdot, DELoader, or Silent Night, operates as a malware loader designed to deploy additional malicious payloads. After nearly two years of inactivity following a massive botnet takedown, the malware resurfaced in September 2023.
The latest variant demonstrates enhanced anti-analysis features and employs a domain generation algorithm to avoid detection. It also includes checks to prevent execution on systems different from the original infected host - a technique borrowed from the Zeus banking trojan that inspired ZLoader's development.
Recent investigations have linked ZLoader distribution to Black Basta ransomware attacks. Threat actors typically deploy the malware through remote desktop connections, often disguising their activities as legitimate technical support operations.
The new version includes an interactive shell allowing operators to execute various commands, including running arbitrary binaries, DLLs, and shellcode. While maintaining HTTPS POST requests as its primary communication method, the addition of DNS tunneling enables the malware to encrypt TLS network traffic using DNS packets.
These updates suggest the threat actors behind ZLoader are actively working to improve their tools for evading detection while serving as initial access brokers for ransomware operations. The malware's continued evolution presents an ongoing challenge for cybersecurity professionals.