The Hidden Risks of Bypassing Wireless Device Restrictions
From AirPods volume limits to regional frequency locks, users increasingly seek ways around wireless device restrictions. Security experts warn that these modifications carry serious technical, legal and safety risks that outweigh potential benefits.
Major Cyberattack Paralyzes Payment Systems Across Israel
A widespread cyberattack disrupted payment processing networks throughout Israel, forcing businesses to halt card transactions and accept only cash. The incident exposed vulnerabilities in critical payment infrastructure while cybersecurity teams worked to restore services and implement additional protections.
Chinese Hackers Rebuild Botnet After FBI Takedown
Volt Typhoon, a Chinese state-sponsored hacking group, is rapidly rebuilding its malware network targeting U.S. critical infrastructure, just weeks after FBI disruption. The group is exploiting vulnerable SOHO routers to recreate its botnet capabilities despite recent law enforcement operations.
North Korean Hackers Deploy FlutterOverflow Malware to Target macOS Users
The notorious Lazarus Group has developed sophisticated macOS malware using Flutter framework to target cryptocurrency exchanges and financial institutions. The malware masquerades as a trading app while enabling data theft and remote system access, marking North Korea's first documented use of Flutter for macOS attacks.
Critical D-Link NAS Vulnerability Left Unpatched, Affecting 61,000+ Devices
D-Link announces no fix for a severe security flaw in over 61,000 NAS devices due to end-of-life status. Users of affected models are urged to take immediate action to protect their data from potential breaches.
Massive Cyberattack Cripples Ahold Delhaize Grocery Chains Across 18 US States
A widespread cyberattack has disrupted operations of Ahold Delhaize USA's grocery brands, affecting pharmacy services, e-commerce, and payment systems across 18 states. The company is working with cybersecurity experts and law enforcement to resolve the issue and ensure customer data security.
Cybercriminals Exploit Exotic Pet Search to Spread Malware
Hackers are targeting users searching for information on Bengal cats in Australia, using SEO poisoning to spread Gootloader malware. Experts warn of the growing trend of exploiting niche searches for cyberattacks.
Russia Warns of Undersea Internet Cable Vulnerabilities, Raising Global Concerns
Russia has issued a stark warning about the vulnerability of undersea internet cables, crucial for global communications. This alert has sparked international discussions on protecting critical infrastructure and balancing open networks with security needs.
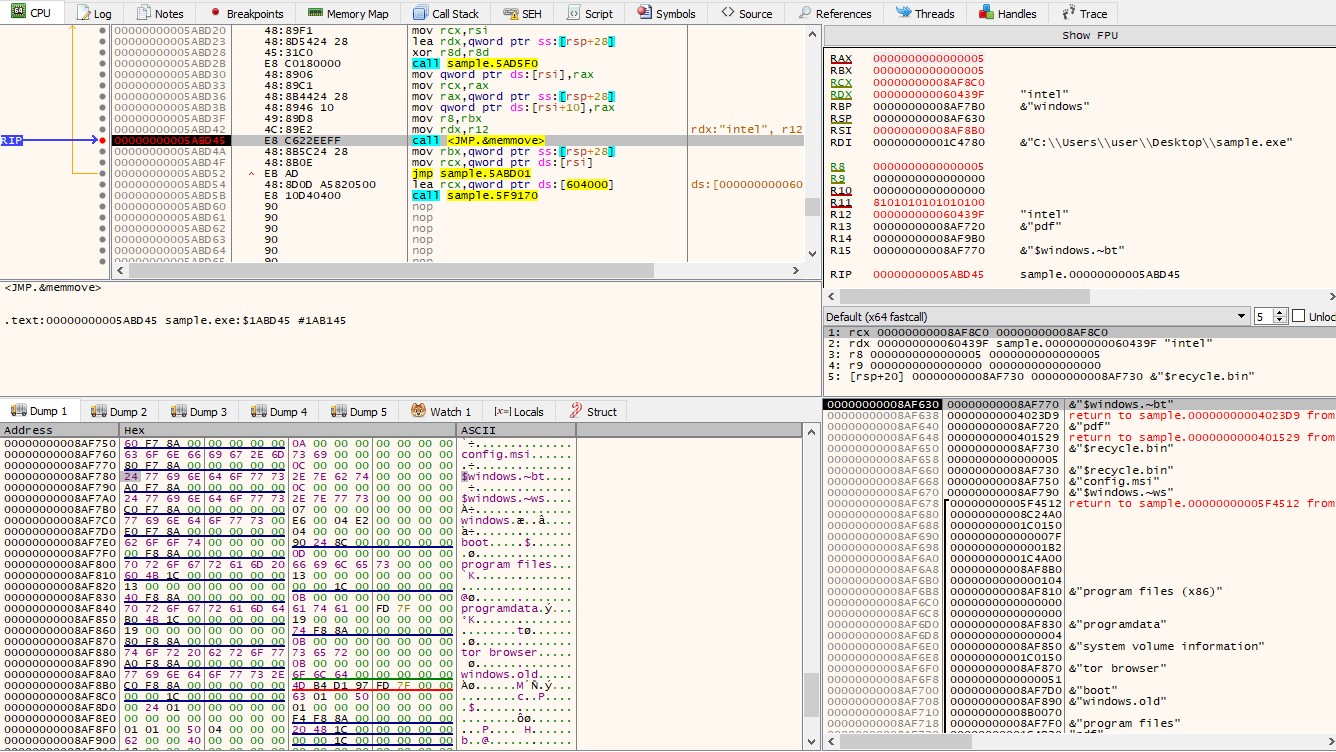
Ymir: The Stealthy Ransomware Revolutionizing Corporate Network Attacks
A new ransomware strain called Ymir is exploiting memory manipulation techniques to evade detection in corporate networks. This innovative malware uses advanced tactics to bypass traditional security measures, signaling a need for enhanced cybersecurity strategies.
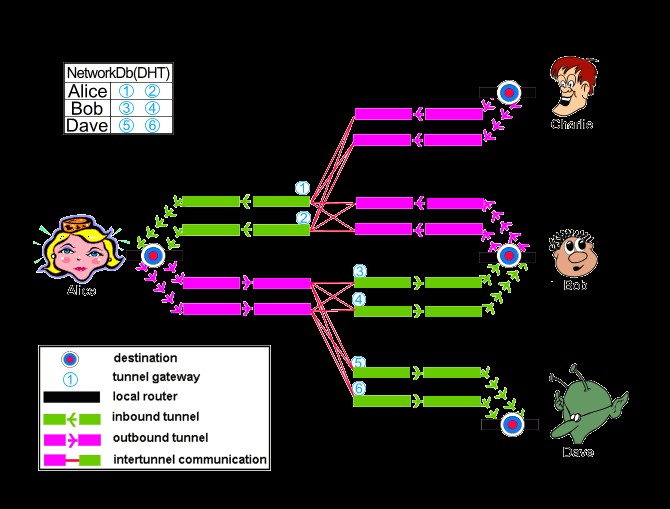
I2P: The Anonymous Network Revolutionizing Online Privacy
Discover how the Invisible Internet Project (I2P) is reshaping online privacy with its encrypted, peer-to-peer network. Learn about its innovative features and community-driven approach to safeguarding digital anonymity.