Apple Faces $1.2B Lawsuit Over Abandoned Child Safety Scanning System
A lawsuit seeking $1.2 billion in damages has been filed against Apple for abandoning planned CSAM detection tools on iCloud. The case, brought by an abuse survivor representing thousands of victims, challenges Apple's balance between user privacy and child protection measures.
Pokemon Go Players Unknowingly Training AI Mapping Systems Through Gameplay
Niantic reveals it's using Pokemon Go player-submitted data to build an AI-powered world mapping system, with over 10 million scanned locations. While beneficial for mapping technology, this data collection raises privacy concerns among cybersecurity experts.
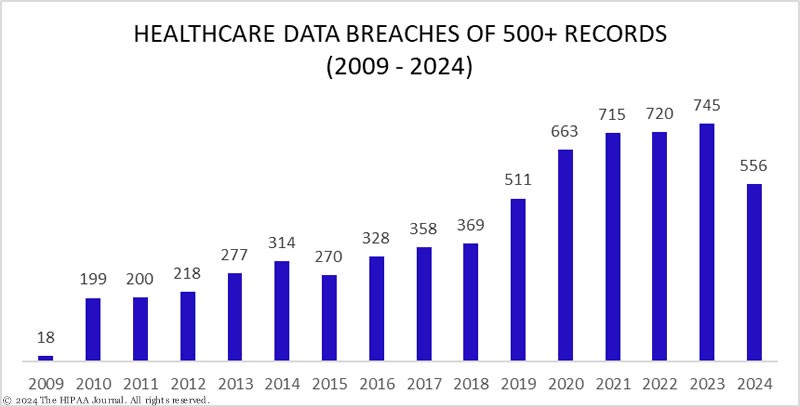
Major French Hospital Data Breach Exposes Medical Records of 750,000 Patients
A devastating cyberattack at the Center Hospitalier Sud Francilien near Paris has compromised sensitive medical data of approximately 750,000 patients spanning two decades. The breach, discovered in August 2022, exposed personal details, social security numbers, and complete medical histories, prompting investigations by French authorities.
US Military Personnel Tracked: Commercial Data Brokers Selling Sensitive Location Data in Germany
A joint investigation reveals that location data of US military and intelligence personnel in Germany is being sold by commercial data brokers, tracking movements from homes to secure facilities including suspected nuclear sites. The legal but concerning practice raises major security risks as anyone can purchase this sensitive information.
Italy's Affordable Spyware Revolution: How Budget-Friendly Surveillance Tools Are Reshaping the Global Market
Italy has emerged as a major player in surveillance technology by offering law enforcement agencies spyware tools for just €150 per day. Unlike premium vendors like NSO Group, Italian firms focus on basic but functional tools, making surveillance technology more accessible while drawing less scrutiny.
T-Mobile Hit by Data Breach in Latest Attack on Telecom Giants
T-Mobile confirms unauthorized access to its systems in a recent cybersecurity incident, marking the latest in a series of attacks targeting major telecommunications providers. The company is working with security experts and law enforcement while advising customers to change passwords and enable two-factor authentication.
Massive Data Breach at Set Forth Exposes 1.5 Million Customers' Personal Information
Set Forth, a major American debt services firm, suffered a significant data breach compromising sensitive data of 1.5 million customers and their families. The company discovered unauthorized system access in May 2024, leading to the theft of personal information including social security numbers.
Digital Self-Defense: A Complete Guide to Protecting Your Privacy from Government Surveillance
Learn essential strategies to shield your digital life from government monitoring in an age of expanding surveillance powers. From encrypted messaging to anonymous browsing, discover practical steps to safeguard your privacy and preserve civil liberties.
The Hidden Risks of Bypassing Wireless Device Restrictions
From AirPods volume limits to regional frequency locks, users increasingly seek ways around wireless device restrictions. Security experts warn that these modifications carry serious technical, legal and safety risks that outweigh potential benefits.
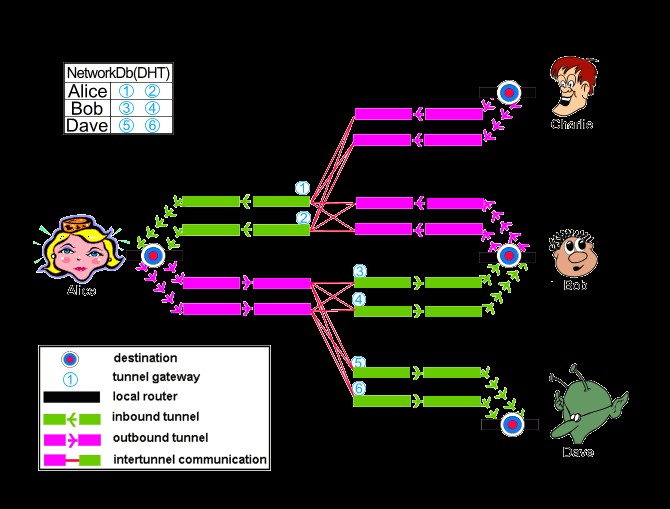
I2P: The Anonymous Network Revolutionizing Online Privacy
Discover how the Invisible Internet Project (I2P) is reshaping online privacy with its encrypted, peer-to-peer network. Learn about its innovative features and community-driven approach to safeguarding digital anonymity.