Featured
NSA's Ghidra 11.3 Brings Major Upgrades Including VS Code Integration and Python Support

The NSA has released version 11.3 of Ghidra, its open-source reverse engineering platform, featuring Visual Studio Code integration and PyGhidra support. The update introduces JIT-accelerated emulation, improved debugging capabilities, and enhanced code analysis tools across Windows, macOS, and Linux.
Critical Security Flaws Exposed in DeepSeek iOS App, Enterprises Urged to Ban Usage

A comprehensive security assessment by NowSecure reveals multiple critical vulnerabilities in the popular DeepSeek iOS app, including unencrypted data transmission and exposure of sensitive information. The findings have prompted urgent calls for enterprise-wide bans as user data faces potential risks from servers in China.
Quantum Teleportation Breakthrough Links Processors for Distributed Computing
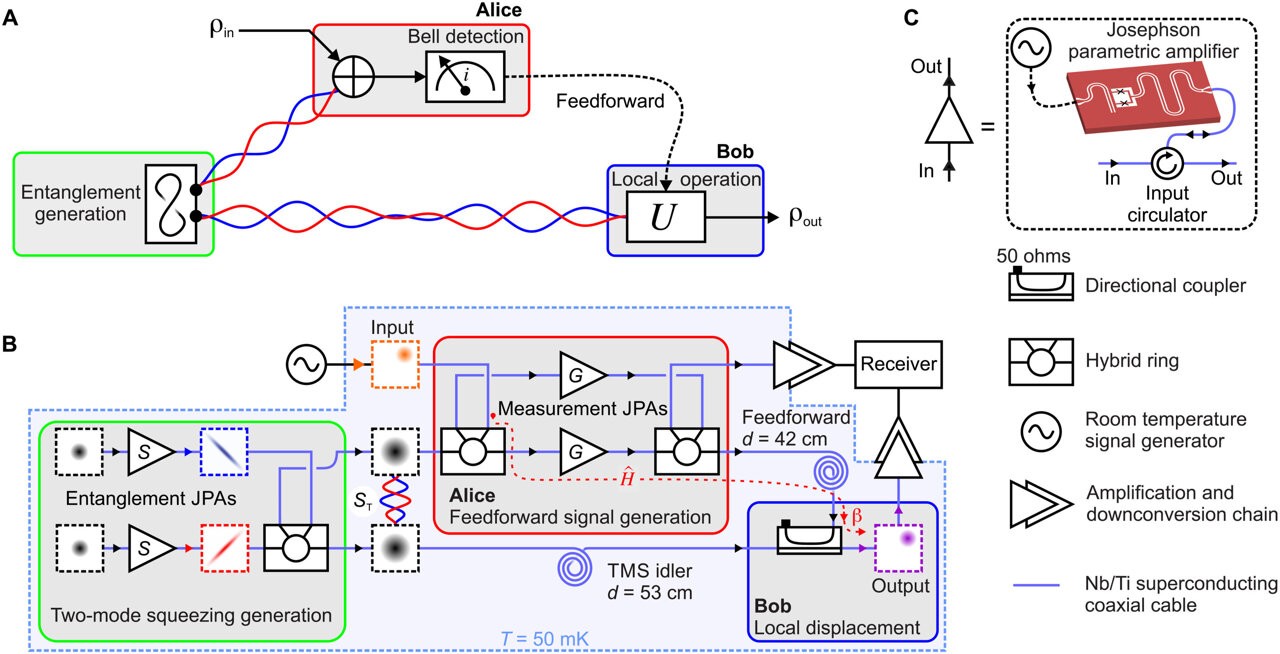
Oxford University researchers achieve quantum teleportation between processors 2 meters apart, enabling distributed quantum computing. The groundbreaking experiment demonstrates quantum gate operations with 70% accuracy using ion traps, marking a crucial step toward scalable quantum computers.
Stanford Researchers Create Powerful AI Model for Just $50, Challenging Industry Giants
Stanford and University of Washington researchers have developed an AI reasoning model for under $50 that rivals million-dollar systems. Using innovative distillation techniques and strategic training data selection, the s1 model demonstrates competitive performance while making AI research more accessible.
Musk's DOGE Team Gains Access to VA Systems, Sparking Privacy Concerns

A representative from Elon Musk's Department of Government Efficiency has been granted access to VA contracting and IT systems, raising alarms about data privacy. Lawmakers and advocates express concerns following similar access granted at the Treasury Department.
Google Shifts AI Ethics Policy, Opens Door to Military Partnerships

Google has quietly removed key passages from its AI principles that previously banned development of potentially harmful AI applications, including weapons. This significant policy change positions the company for increased military collaboration, marking a departure from its original ethical stance.
Abandoned AWS Storage Buckets: A Critical Supply Chain Attack Risk
Security researchers reveal how abandoned AWS S3 storage buckets can be exploited for large-scale cyberattacks, potentially enabling SolarWinds-like supply chain compromises. The study found approximately 150 deserted buckets previously used by major organizations receiving millions of file requests.
Critical Security Flaw: Go Module Mirror Served Malicious Package for Three Years
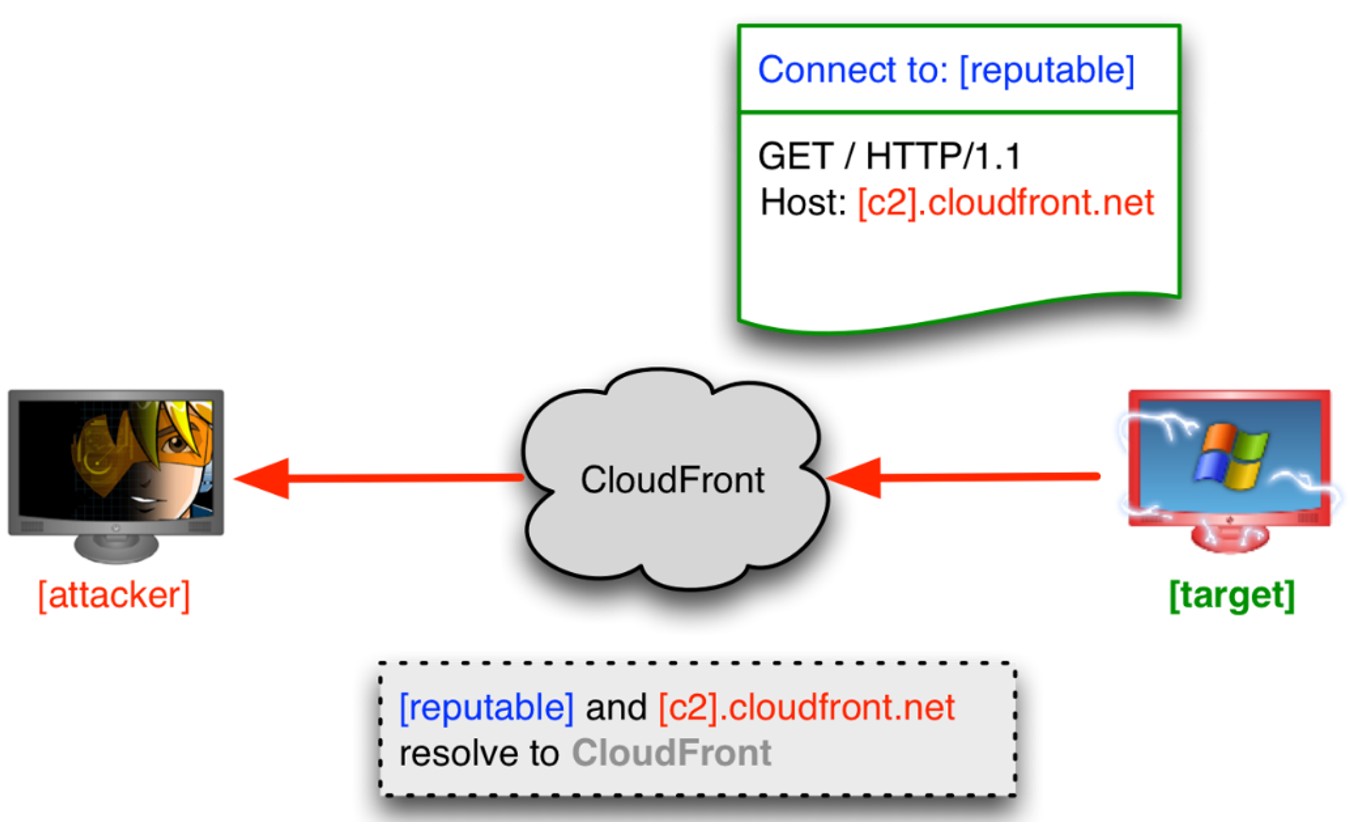
A major security breach in Google's Go Module Mirror exposed developers to a sophisticated backdoored package masquerading as a popular library for over three years. The malicious typosquatting attack potentially compromised thousands of development environments through remote command execution capabilities.
Australia Bans Chinese AI Chatbot DeepSeek from Government Systems Over Security Concerns

Australia has banned DeepSeek, a Chinese AI chatbot, from federal government devices citing national security risks and data handling concerns. The move follows similar restrictions by other nations and reflects growing scrutiny of Chinese technology platforms.