Featured
Chinese AI Startup DeepSeek Restricts Sign-ups After Major Cyberattack Amid Rapid Growth

DeepSeek, a rising Chinese AI company, temporarily halts new user registrations following large-scale malicious attacks on its platform. The startup has recently overtaken ChatGPT in App Store downloads and gained attention for its cost-effective R1 model development.
Russian Cyber Espionage Campaign Unmasked: GamaCopy Group Mimics Kremlin-Linked Tactics

A new hacking group dubbed GamaCopy has been discovered impersonating Russian state-backed Gamaredon's tactics to infiltrate Russian-speaking targets. The group deploys UltraVNC remote access tools through sophisticated phishing campaigns, joining other threat actors targeting Russian organizations amid the Ukraine conflict.
Baltic Sea Cable Sabotage: Latvia-Sweden Link Damaged as NATO Boosts Maritime Security

A critical undersea fiber-optic cable connecting Latvia and Sweden was damaged in the Baltic Sea, prompting criminal investigations and military response. The incident, suspected to be deliberate sabotage, adds to recent attacks on regional infrastructure as NATO deploys resources to protect maritime assets.
Essential Smartphone Security Guide for Protesters: Protecting Your Digital Rights

A comprehensive guide to securing smartphones during protests, covering crucial pre-event preparation, real-time best practices, and post-demonstration data protection. Learn how to safeguard your device, privacy, and fellow protesters while documenting important moments.
EU Launches Social Media 'Stress Test' to Combat Election Disinformation

The European Commission will evaluate major tech platforms' readiness to fight disinformation before German elections in February. Seven tech giants including Meta, TikTok, and X will participate in simulated scenarios testing their compliance with EU's Digital Services Act.
NIH Freezes Operations: Unprecedented Halt in Medical Research Review Process

The National Institutes of Health has implemented an abrupt freeze on grant reviews and external communications, throwing the medical research community into disarray. Leading scientists express alarm as the suspension threatens to delay critical research funding and medical advances.
Historic Healthcare Breach: UnitedHealth Cyberattack Exposes 190 Million Americans' Medical Records
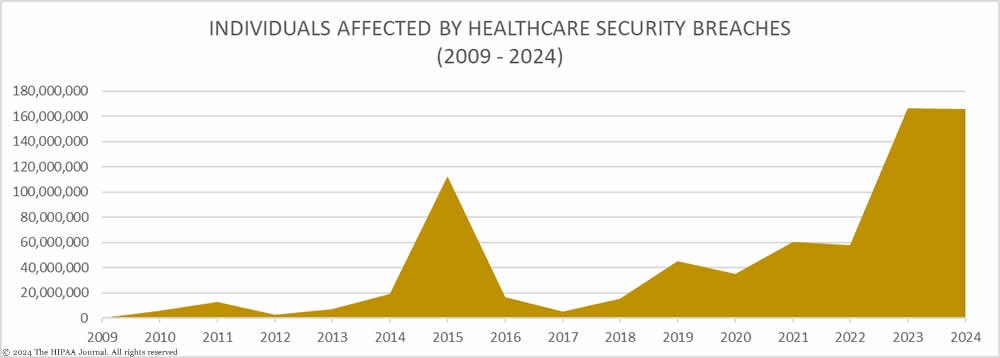
UnitedHealth Group reveals that a devastating ransomware attack on Change Healthcare compromised sensitive medical and personal data of approximately 190 million Americans. The breach, attributed to the Russian-linked ALPHV group, marks the largest medical data breach in U.S. history.
Critical Alert: J-magic Malware Targets Enterprise Networks Through Juniper Router Vulnerabilities

A sophisticated malware campaign dubbed J-magic is actively compromising corporate networks by targeting Juniper routers running JunoOS. The attacks use a custom backdoor that creates reverse shell access when triggered by magic packets, with infections detected across 36 global IP addresses.
Critical jQuery Vulnerability Added to CISA's Known Exploited List Despite 4-Year-Old Patch
CISA has added a medium-severity jQuery vulnerability to its Known Exploited Vulnerabilities catalog due to active exploitation in the wild. The vulnerability, patched in 2020, allows attackers to execute malicious code through cross-site scripting despite existing HTML sanitization.





