Featured
Apple Revolutionizes Photo Privacy with Homomorphic Encryption in iOS18
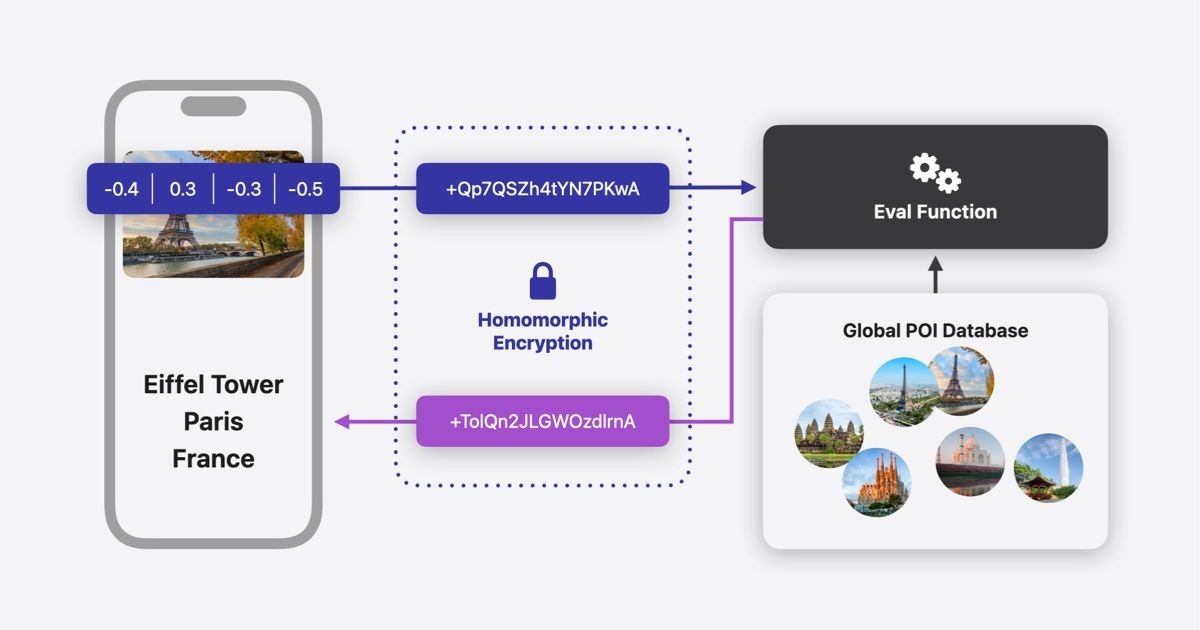
Apple introduces groundbreaking privacy-preserving search in iOS 18's Photos app using homomorphic encryption, allowing users to search images without exposing data to servers. The innovative 'Wally' system processes encrypted queries while maintaining complete user privacy.
Brad Pitt AI Deepfakes Used to Scam French Woman Out of $850,000

A French interior designer lost her marriage and life savings after falling victim to an elaborate romance scam using AI-generated images of Brad Pitt. The 18-month deception involved fraudsters posing as Pitt's mother and requesting money for alleged medical treatments and customs fees.
FBI Launches Unprecedented Operation to Purge Chinese PlugX Malware from US Networks

In a groundbreaking cybersecurity operation, the FBI successfully removed dangerous Chinese PlugX malware from over 4,000 US computers by exploiting its self-delete function. Working with French authorities, the agency leveraged compromised command servers to cleanse infected systems nationwide.
EU Challenges US Export Controls on AI Chips Amid Global Technology Tensions

The European Union strongly opposes new US restrictions creating a tiered system for AI chip access among EU member states. While ten nations receive privileged 'Tier 1' status, others face strict GPU limitations, sparking concerns over innovation and transatlantic technology trade relations.
Digital Deplatforming: Business Owner Banned After Satirical CEO Playing Cards Announcement

A business owner faced widespread account removals and platform bans after announcing plans to sell satirical playing cards featuring CEOs. The incident highlights contentious issues around content moderation policies and platform control over online expression.
AWS Cloud Storage at Risk: New Ransomware Weaponizes S3 Encryption Features
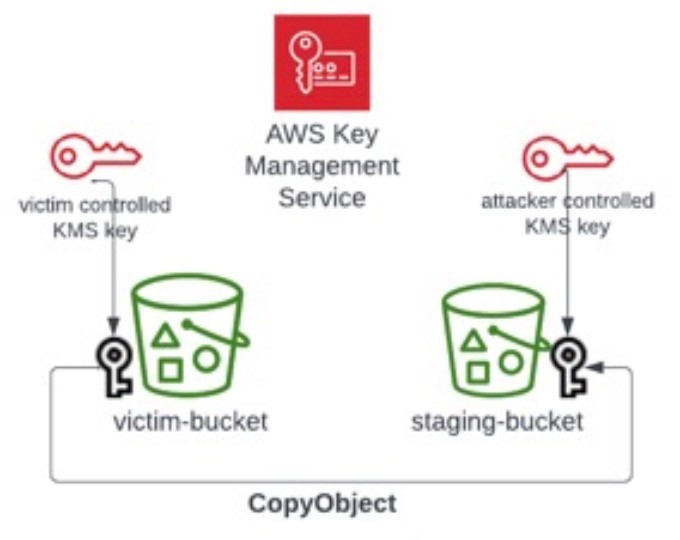
A sophisticated ransomware group called Codefinger is exploiting AWS's native encryption features to lock down S3 buckets, marking a concerning evolution in cloud-based attacks. The group leverages stolen credentials and legitimate AWS functionality to encrypt data, making recovery impossible without the attacker's key.
UK Moves to Ban Public Sector Ransomware Payments in Landmark Cybersecurity Push

The UK government proposes groundbreaking legislation to prohibit ransomware payments by public sector organizations and critical infrastructure companies. The initiative, which includes mandatory reporting requirements, aims to disrupt cybercriminal operations that collected an estimated $1 billion globally in 2023.
Developer Creates Playable Version of Doom Inside PDF Document

A creative developer has managed to port the iconic 1993 game Doom to run directly within PDF files using browser-based JavaScript. This innovative implementation allows players to experience the classic first-person shooter through keyboard controls, adding another fascinating chapter to Doom's technical legacy.
Proton's Global Service Disruption: Lessons from a Complex Infrastructure Migration
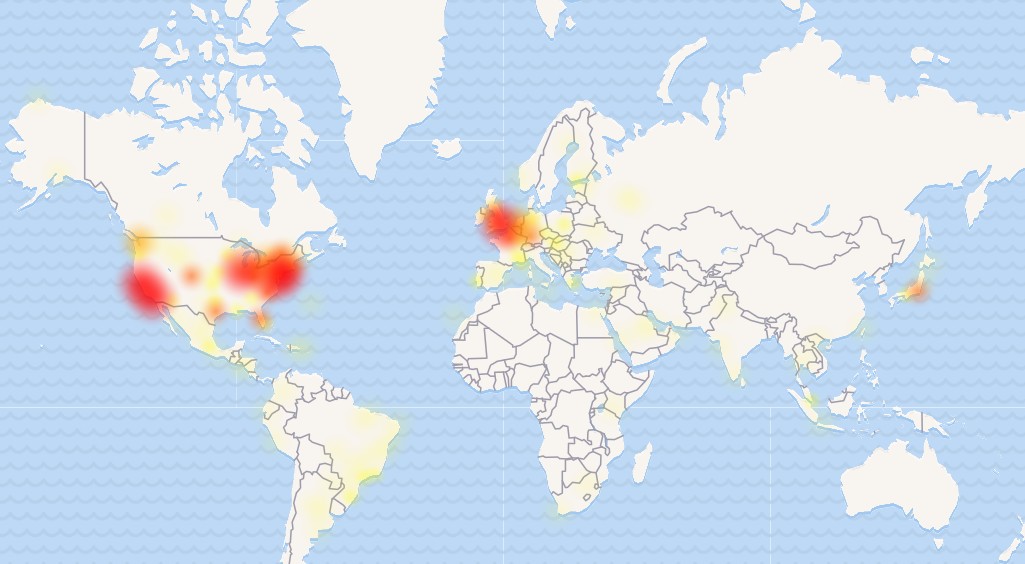
A major outage struck Proton's services during an ambitious transition to Kubernetes infrastructure, affecting users worldwide. The incident exposed critical challenges in modernizing technical systems while highlighting important lessons for maintaining service stability during complex upgrades.





