Featured
China-Linked APT Group Deploys Novel Linux Backdoors for Cyber Espionage

Security researchers have uncovered two sophisticated Linux backdoors - WolfsBane and FireWood - linked to Chinese state-sponsored hackers. The discovery marks a significant shift in APT tactics toward Linux-based malware, enabling stealthy system compromise and data theft across Asia.
Massive Security Breach: Over 2,000 Palo Alto Networks Firewalls Compromised in Global Attack
Security researchers have uncovered 'Operation Lunar Peek', a widespread attack campaign targeting Palo Alto Networks devices worldwide. The attacks exploit critical vulnerabilities in next-generation firewall management interfaces, with over 2,000 devices already compromised across multiple countries.
Major French Hospital Data Breach Exposes Medical Records of 750,000 Patients
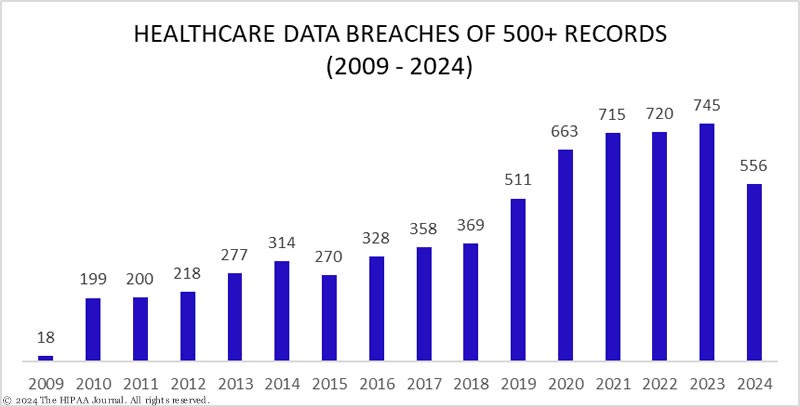
A devastating cyberattack at the Center Hospitalier Sud Francilien near Paris has compromised sensitive medical data of approximately 750,000 patients spanning two decades. The breach, discovered in August 2022, exposed personal details, social security numbers, and complete medical histories, prompting investigations by French authorities.
AI-Generated Instagram Accounts Exploit Real Content Creators in Growing 'AI Pimping' Trend

A disturbing rise in AI-modified Instagram accounts are misappropriating content from legitimate creators and redirecting followers to monetization channels. The sophisticated operation involves thousands of synthetic profiles using AI tools, threatening authentic creators' livelihoods while raising concerns about content ownership and platform responsibility.
FBI Charges Five Young Hackers in Scattered Spider Cybercrime Investigation

US authorities have charged five individuals aged 19-24 linked to the Scattered Spider cybercrime group, known for sophisticated social engineering attacks against major tech companies. The group allegedly compromised corporate networks through employee manipulation and SIM swapping, causing millions in damages.
Apple Patches Critical Zero-Day Vulnerabilities Under Active Attack in macOS

Apple has issued emergency security updates to address actively exploited zero-day vulnerabilities affecting macOS systems, which could grant attackers kernel-level access. The critical flaws impact both Intel and Apple Silicon Macs, prompting urgent calls for users to update their systems immediately.
Apple Patches Critical Zero-Day Vulnerability Under Active Exploitation in macOS

Apple has confirmed active exploitation of a critical zero-day vulnerability affecting multiple macOS versions, allowing attackers to gain system-level access to devices. The company has released an urgent security update while investigating targeted attacks leveraging this kernel-level flaw.
US Military Personnel Tracked: Commercial Data Brokers Selling Sensitive Location Data in Germany

A joint investigation reveals that location data of US military and intelligence personnel in Germany is being sold by commercial data brokers, tracking movements from homes to secure facilities including suspected nuclear sites. The legal but concerning practice raises major security risks as anyone can purchase this sensitive information.
Global Law Enforcement Dismantles Massive Residential Proxy Botnet Operation
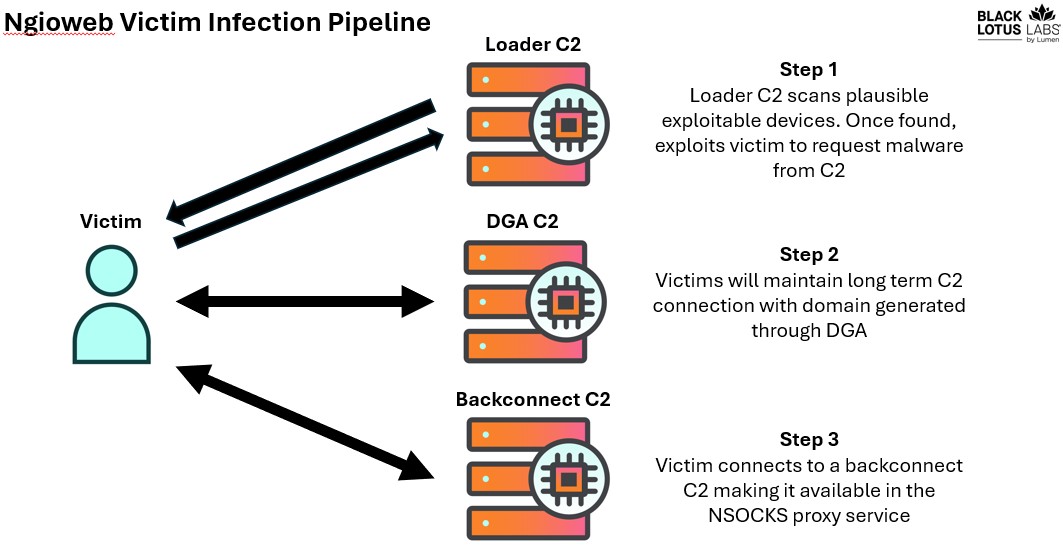
International authorities have disrupted a sophisticated botnet that hijacked hundreds of thousands of home computers to create an illegal proxy network for cybercriminals. The operation dealt a significant blow to cybercrime infrastructure while recovering millions in illicit profits and seized assets.





