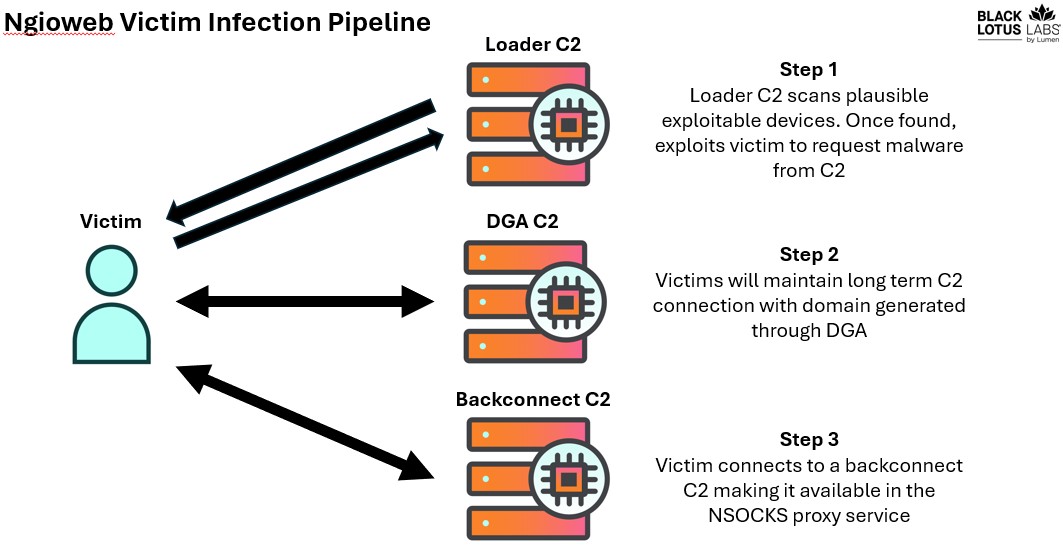
Global Law Enforcement Dismantles Massive Residential Proxy Botnet Operation
International authorities have disrupted a sophisticated botnet that hijacked hundreds of thousands of home computers to create an illegal proxy network for cybercriminals. The operation dealt a significant blow to cybercrime infrastructure while recovering millions in illicit profits and seized assets.
Hackers Exploit Unsecured Jupyter Notebooks for Illegal Sports Streaming Operation
Cybersecurity researchers discovered hackers compromising poorly secured Jupyter Notebooks to illegally stream sports content from beIN Sports. The attack pattern involves installing FFmpeg for capturing and redistributing broadcasts, highlighting broader security risks beyond piracy.
Russian Ransomware Groups Recruiting Penetration Testers to Enhance Attack Capabilities
Russian cybercrime gangs are actively seeking skilled penetration testers on underground forums to strengthen their ransomware operations. The concerning trend, revealed in a Cato Networks report, highlights the growing professionalization of ransomware attacks and lowering barriers to entry in cybercrime.
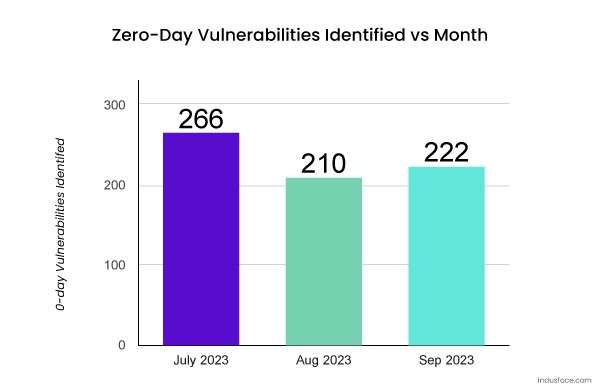
Zero-Day Vulnerabilities Dominated Cyber Attacks in 2023, Five Eyes Report Reveals
A new intelligence report shows zero-day exploits became the primary attack vector for cybercriminals in 2023, marking a significant shift from previous years. The findings highlight the growing sophistication of threat actors targeting enterprise networks and emphasize the critical need for rapid vulnerability patching.
Foreign Hackers Breach Library of Congress Email Systems in Major Cyber Espionage Attack
A sophisticated cyber attack has compromised months of sensitive email communications between the Library of Congress and congressional offices. The breach, conducted by an unidentified foreign adversary, exposed correspondence containing confidential legislative proposals from January to September 2023.
Critical WordPress Security Plugin Flaw Exposes Millions of Sites to Admin Takeover
A severe vulnerability in a widely-used WordPress security plugin puts millions of websites at risk of complete administrative compromise. Site owners are urged to immediately update their plugins and audit admin accounts as researchers warn of potential unauthorized access and data exposure.
Chinese Hackers Deploy DEEPDATA Malware to Target Fortinet VPN Users
Security researchers uncover sophisticated malware operation by BrazenBamboo targeting FortiClient through an unpatched vulnerability. The attack uses a modular framework to steal VPN credentials and sensitive data, with potential links to Chinese cyber espionage activities.
EPA Report Reveals Critical Cybersecurity Gaps in US Water Infrastructure
A concerning EPA watchdog investigation has uncovered major cybersecurity vulnerabilities in drinking water systems serving 193 million Americans. The report highlights inadequate security protocols and emergency response planning, raising alarms about potential cyber attacks that could disrupt or contaminate water supplies.
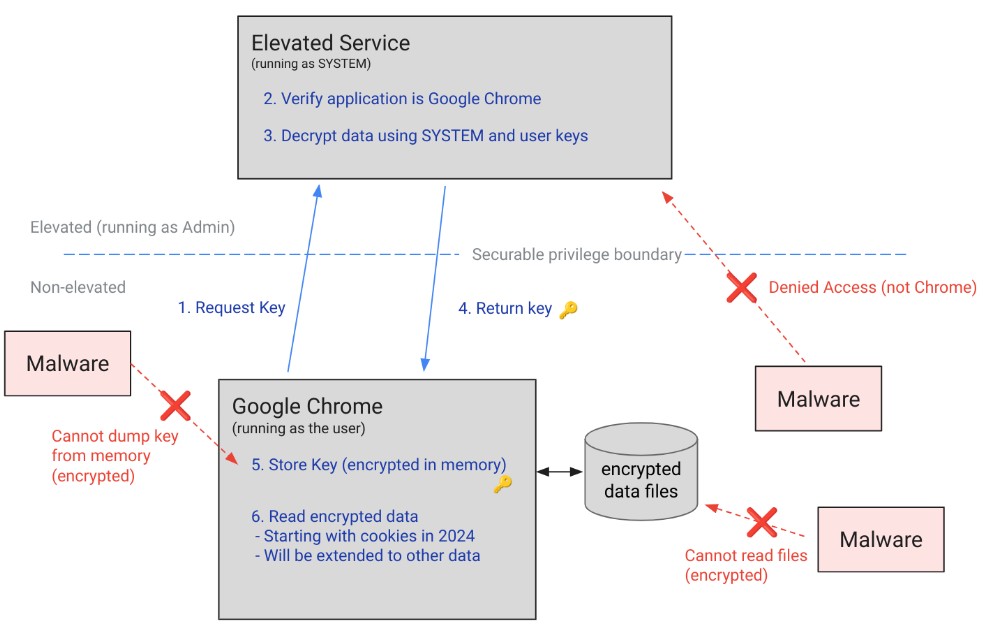
New Chrome Malware Bypasses Cookie Encryption, Exposing User Data
A sophisticated new malware strain can circumvent Google Chrome's cookie encryption mechanisms, allowing cybercriminals to silently harvest sensitive login credentials and session data. The concerning development highlights vulnerabilities in browser security and prompts recommendations for enhanced user protection.
Malicious GitHub Commits Target Security Researcher in Identity Fraud Attack
Multiple open-source projects on GitHub were compromised by unauthorized code commits falsely attributed to security researcher Stephen Lacy. The attack exploited commit verification weaknesses to damage the researcher's reputation, prompting GitHub to investigate and the community to implement stricter authentication measures.