Critical Vulnerabilities Allow Root Access to Palo Alto Firewalls Through Authentication Bypass
Multiple security flaws in Palo Alto Networks firewalls are being actively exploited to gain unauthorized root access. Attackers are chaining together several vulnerabilities, including a recent high-severity authentication bypass, putting sensitive system data at risk.
Google Chrome Rolls Out AI-Powered Security Shield Against Emerging Threats
Chrome's Enhanced Protection feature now leverages artificial intelligence to detect and block malicious websites, downloads, and extensions in real-time across all platforms. This major security upgrade follows successful testing and comes amid recent attacks that compromised multiple Chrome extensions.
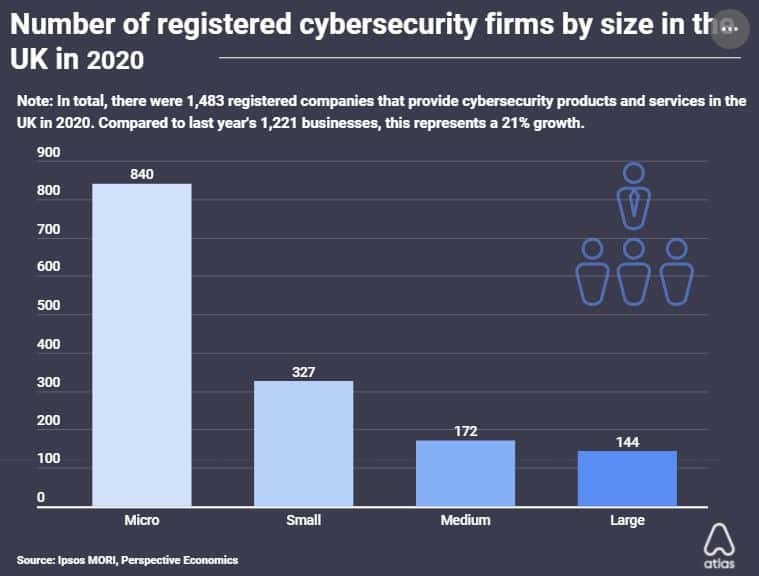
UK Cybersecurity Report Reveals £11.9B Industry Growth Amid Rising Digital Threats
New data shows cyber attacks impacting up to 74% of UK businesses, with ransomware emerging as the leading threat. The cybersecurity sector continues robust growth, generating £11.9 billion in revenue while confronting evolving challenges across energy, technology, and government sectors.
Ransomware Attack Cripples Michigan Tribal Nation's Critical Services and Casinos
A devastating ransomware attack has forced Michigan's largest federally-recognized tribe to shut down multiple facilities, including five casinos and health centers. The Sault Tribe's 44,000 members face disrupted medical services and community operations as officials work with cybersecurity experts to restore systems.
Browser Syncjacking: The Dangerous New Chrome Attack That Hijacks Your Entire Computer
Researchers uncover 'browser syncjacking', a sophisticated cyberattack that uses malicious Chrome extensions to gain complete control of victims' devices. The attack exploits Google's browser sync feature to steal sensitive data while evading detection through legitimate-looking prompts and minimal permissions.
XE Group Evolves from Card Skimming to Zero-Day Exploitation in Supply Chain Attacks
Notorious cybercrime group XE Group has shifted tactics from credit card theft to exploiting critical vulnerabilities in supply chain software. The group now leverages sophisticated zero-day exploits and web shells to maintain long-term unauthorized access to manufacturing and distribution systems.
DeepSeek AI Model Raises Bioweapons Safety Concerns in Anthropic Testing
Anthropic CEO reveals alarming test results showing Chinese AI company DeepSeek's model performed poorly on bioweapons safety evaluations, lacking protective barriers against dangerous content. The findings have prompted bans from military organizations while major cloud providers continue integration.
Security Flaws in CONTEC Patient Monitors Raise Healthcare Data Concerns
Recent regulatory alerts about potential backdoors in Chinese-made CONTEC CMS8000 patient monitors reveal serious but unintentional security vulnerabilities. Research shows poor security design enables data leakage and remote code execution risks, requiring healthcare providers to implement strict network controls.
Critical Security Flaws Exposed in DeepSeek iOS App, Enterprises Urged to Ban Usage
A comprehensive security assessment by NowSecure reveals multiple critical vulnerabilities in the popular DeepSeek iOS app, including unencrypted data transmission and exposure of sensitive information. The findings have prompted urgent calls for enterprise-wide bans as user data faces potential risks from servers in China.
Abandoned AWS Storage Buckets: A Critical Supply Chain Attack Risk
Security researchers reveal how abandoned AWS S3 storage buckets can be exploited for large-scale cyberattacks, potentially enabling SolarWinds-like supply chain compromises. The study found approximately 150 deserted buckets previously used by major organizations receiving millions of file requests.