Critical SimpleHelp RMM Vulnerabilities Exploited to Deploy Sliver Malware
Hackers are actively exploiting security flaws in SimpleHelp's Remote Monitoring and Management software to gain unauthorized network access and deploy malicious tools. The campaign, discovered by Field Effect researchers, leverages recently patched vulnerabilities that could enable system compromise if left unpatched.
Critical Security Flaw: Go Module Mirror Served Malicious Package for Three Years
A major security breach in Google's Go Module Mirror exposed developers to a sophisticated backdoored package masquerading as a popular library for over three years. The malicious typosquatting attack potentially compromised thousands of development environments through remote command execution capabilities.
Casio UK Website Hit by Sophisticated Payment Skimming Attack
Casio's UK online store suffered a major security breach exposing customer payment data through an advanced web skimmer attack between January 14-24, 2025. The sophisticated scheme used fake payment forms to harvest sensitive information before routing victims to legitimate checkout pages.
Brazilian Banking Malware 'Coyote' Expands Target List to Over 1,000 Financial Sites
A sophisticated Windows malware strain called Coyote has dramatically expanded its attack scope, now targeting over 1,030 websites and 73 financial institutions in Brazil. The threat employs advanced techniques including keylogging, screenshot capture, and phishing overlays to steal sensitive credentials.
Russian Cyber Espionage Campaign Unmasked: GamaCopy Group Mimics Kremlin-Linked Tactics
A new hacking group dubbed GamaCopy has been discovered impersonating Russian state-backed Gamaredon's tactics to infiltrate Russian-speaking targets. The group deploys UltraVNC remote access tools through sophisticated phishing campaigns, joining other threat actors targeting Russian organizations amid the Ukraine conflict.
Critical Alert: J-magic Malware Targets Enterprise Networks Through Juniper Router Vulnerabilities
A sophisticated malware campaign dubbed J-magic is actively compromising corporate networks by targeting Juniper routers running JunoOS. The attacks use a custom backdoor that creates reverse shell access when triggered by magic packets, with infections detected across 36 global IP addresses.
Global Password Security Crisis: Malware Steals Over 1 Billion Credentials in 2024
A staggering report reveals malware attacks led by Redline, Vidar, and Raccoon Stealer compromised over 1 billion passwords in 2024, despite strong complexity measures. The unprecedented breach highlights critical weaknesses in traditional password security approaches and urgent need for modern protection strategies.
PowerSchool Data Breach Exposes Complete Historical Records of Students and Teachers
PowerSchool, a major education technology provider, confirms unauthorized access to its Student Information System led to comprehensive theft of current and former student and teacher data. The breach exposed sensitive information including personal details, medical records and academic data across multiple school districts.
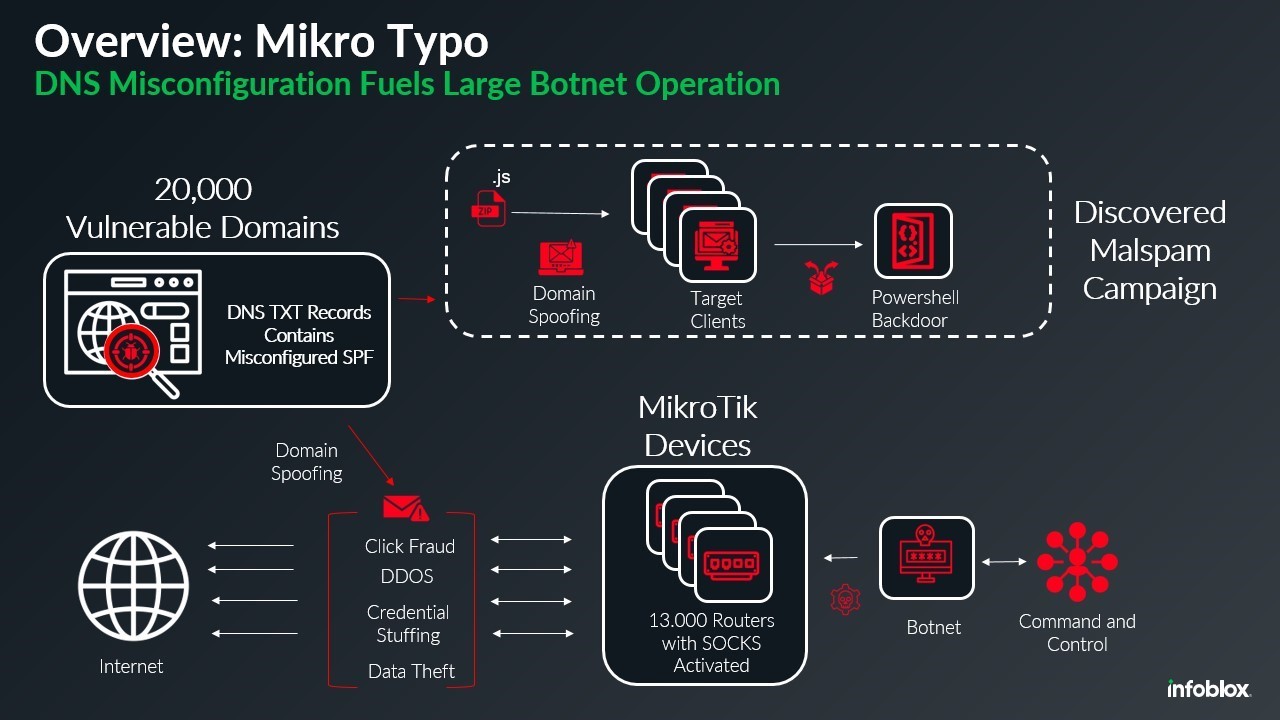
Massive MikroTik Router Botnet Exploits DNS Flaws to Launch Malware Campaign
A sophisticated botnet comprising 13,000 hijacked MikroTik routers is exploiting DNS misconfigurations to distribute malware while impersonating legitimate domains. The campaign uses compromised devices as SOCKS proxies to bypass email security and deliver malicious payloads through spoofed shipping notifications.
FBI Launches Unprecedented Operation to Purge Chinese PlugX Malware from US Networks
In a groundbreaking cybersecurity operation, the FBI successfully removed dangerous Chinese PlugX malware from over 4,000 US computers by exploiting its self-delete function. Working with French authorities, the agency leveraged compromised command servers to cleanse infected systems nationwide.