New Linux-Targeting UEFI Bootkit Discovered: BootKitty Exploits LogoFAIL Vulnerability
Security researchers have identified BootKitty, one of the first UEFI bootkits specifically designed to compromise Linux systems by exploiting firmware vulnerabilities. The sophisticated malware can persist after OS reinstallation and demonstrates concerning capabilities in bypassing kernel security measures.
First Linux UEFI Bootkit 'Bootkitty' Discovered, Marking New Era in Linux Threats
Security researchers at ESET have uncovered 'Bootkitty', the first known UEFI bootkit targeting Linux systems. While still in development, this sophisticated malware can infect startup processes and signals an emerging wave of Linux-focused cyber threats.
Bootkitty: First UEFI Bootkit Malware Targeting Linux Systems Discovered
Security researchers have identified Bootkitty, a groundbreaking UEFI bootkit malware specifically designed to target Linux systems. This proof-of-concept malware can disable kernel signature verification and persist through OS reinstallation, marking a concerning evolution in firmware-level threats.
Critical Vulnerabilities in WordPress Anti-Spam Plugin Put 200,000 Sites at Risk
Two severe security flaws discovered in the Anti-Spam by CleanTalk WordPress plugin could allow attackers to gain unauthorized control of over 200,000 websites. The developer has released patches while security researchers implement protective measures for affected installations.
Russian Hacking Group RomCom Exploits Firefox Zero-Days in Sophisticated Attack Campaign
A Russian cybercrime group has launched major attacks across Europe and North America by exploiting critical Firefox and Tor Browser vulnerabilities. The sophisticated campaign infected systems through maliciously crafted websites, demonstrating RomCom's advanced capabilities and evolving tactics.
Critical VPN Client Vulnerabilities Allow Attackers to Deploy Malware Through Fake Servers
Security researchers have discovered severe flaws in Palo Alto Networks' GlobalProtect and SonicWall's NetExtender VPN clients that enable attackers to execute malicious code through rogue VPN servers. The vulnerabilities could allow credential theft and system compromise through unauthorized software updates with elevated privileges.
Zero-Click Attack: RomCom Hackers Chain Firefox and Windows Flaws in Sophisticated Campaign
Russian-aligned RomCom hackers exploited two zero-day vulnerabilities in Firefox and Windows to silently compromise systems across Europe and North America. The sophisticated attack required no user interaction, highlighting the growing capabilities of state-sponsored threat actors.
Ransomware Attack on Blue Yonder Cripples Major Retail Supply Chains
A devastating ransomware attack on supply chain software provider Blue Yonder has forced major retailers like Starbucks to resort to manual operations. The incident, occurring during the peak Thanksgiving period, has disrupted warehouse management and retail operations across the U.S. and UK.
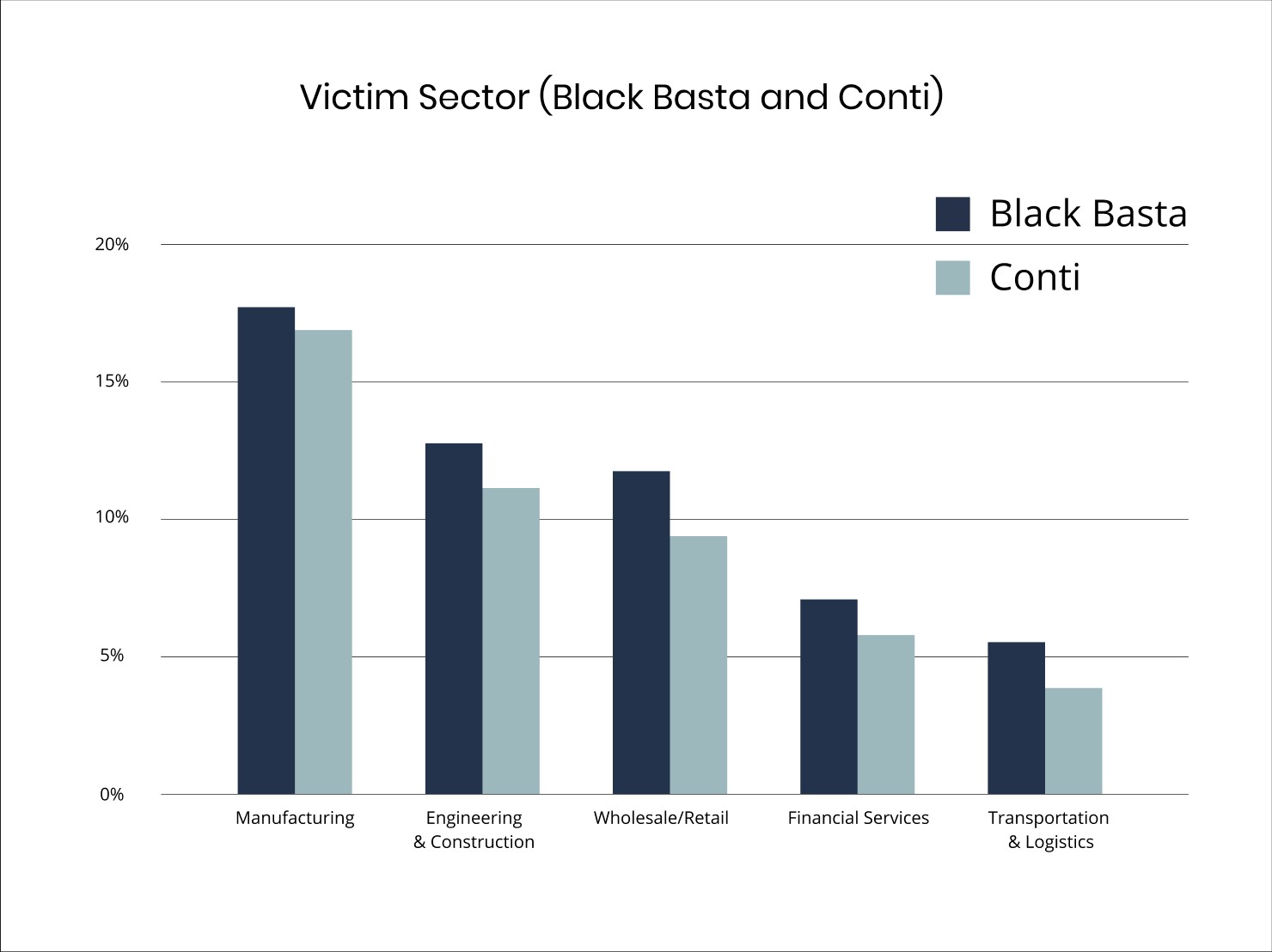
BlackBasta: The Rising Ransomware Empire Filling Conti's Void
Following Conti's downfall, BlackBasta has emerged as a formidable force in Russian ransomware operations, showcasing remarkable adaptability through custom malware tools and sophisticated attack methods. The group's targeting of healthcare sectors and potential ties to state actors signal an evolving threat landscape requiring enhanced cybersecurity measures.
Hackers Exploit Avast Driver Vulnerability to Disable Antivirus Protection
Security researchers have discovered malware that hijacks Avast's anti-rootkit driver to terminate antivirus processes on infected systems. The sophisticated attack, active since 2021, targets 142 security products and uses a bring-your-own-vulnerable-driver technique to compromise system defenses.