Featured
Lazarus Group Develops Stealthy macOS Malware Using Extended Attributes
North Korean hackers have created RustyAttr, a sophisticated malware that hides within macOS metadata to evade detection. Built with Tauri framework, this innovative technique allows malicious code to bypass security measures while using deceptive tactics to target cryptocurrency users.
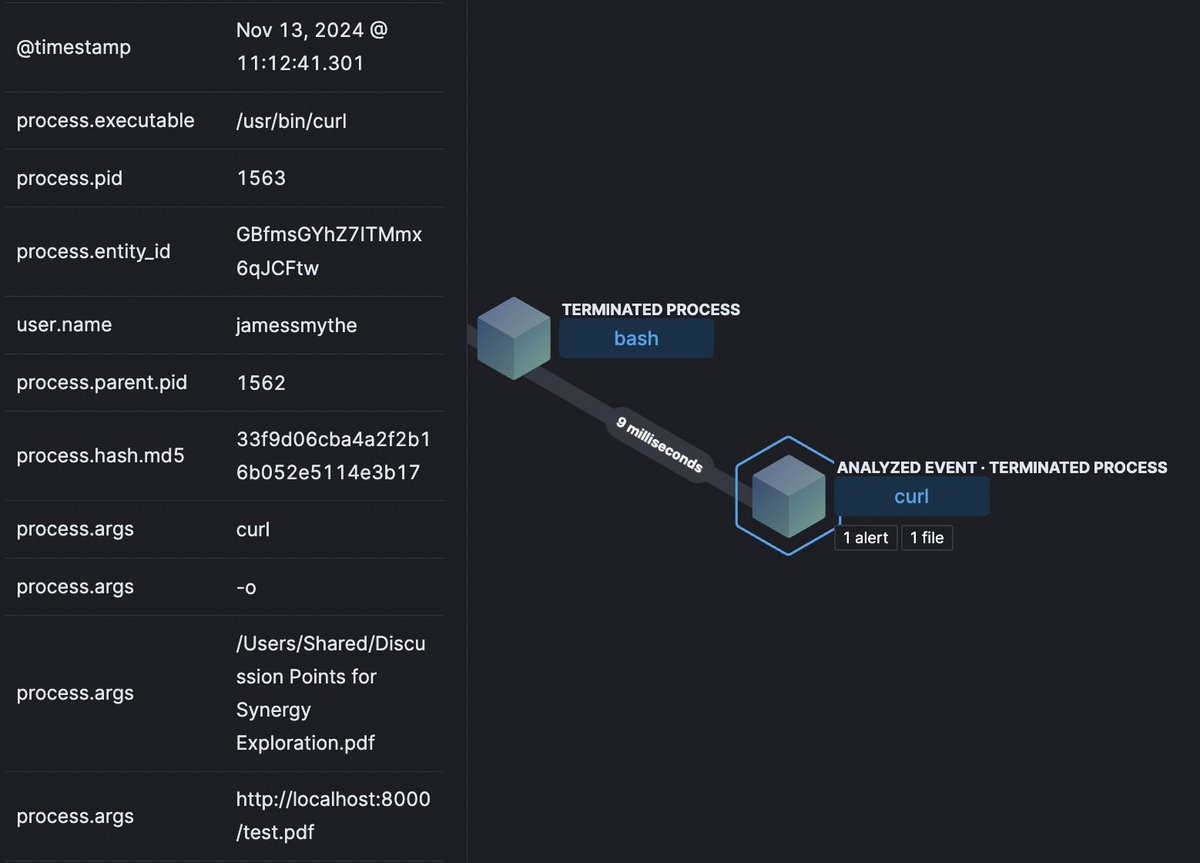
Critical Backdoor Attempt Detected in ExoLabs GitHub Repository
A malicious pull request containing backdoor code was discovered in the popular ExoLabs GitHub repository, highlighting the growing threat of supply chain attacks. The incident serves as a crucial reminder for maintainers to implement strict code review protocols and security measures.
Teen Swatting Mastermind Faces Prison After Orchestrating 375+ Hoax Emergency Calls

An 18-year-old California teen has pleaded guilty to federal charges for conducting one of America's largest swatting campaigns, targeting schools, religious institutions, and government officials. Operating as 'Torswats,' he ran a swatting-for-hire operation that caused widespread fear and chaos across communities.
Amazon Employee Data Exposed in Third-Party MOVEit Security Breach

Amazon confirms exposure of over 2.8 million employee records through a third-party vendor's MOVEit vulnerability. While sensitive financial data remained secure, the breach leaked work-related information and adds Amazon to a growing list of organizations impacted by MOVEit attacks.
Massive Data Breach at Set Forth Exposes 1.5 Million Customers' Personal Information

Set Forth, a major American debt services firm, suffered a significant data breach compromising sensitive data of 1.5 million customers and their families. The company discovered unauthorized system access in May 2024, leading to the theft of personal information including social security numbers.
Digital Self-Defense: A Complete Guide to Protecting Your Privacy from Government Surveillance

Learn essential strategies to shield your digital life from government monitoring in an age of expanding surveillance powers. From encrypted messaging to anonymous browsing, discover practical steps to safeguard your privacy and preserve civil liberties.
Tech Enthusiasts Hack AirPods Pro 2 Hearing Aid Restrictions Using DIY Faraday Cage

Indian tech enthusiasts develop an innovative workaround using a homemade Faraday cage to unlock AirPods Pro 2's region-locked hearing aid features. The community initiative helps provide affordable hearing assistance where traditional devices remain cost-prohibitive.
Israeli Payment Systems Paralyzed by DDoS Attack Amid Rising Regional Tensions

A sophisticated DDoS attack on Hyp Credit Guard's payment gateway disrupted card transactions across Israel, affecting gas stations, supermarkets, and transportation services. While no data was compromised, the incident highlights escalating cyber threats against Israeli infrastructure, with Iran-linked hackers claiming responsibility.
Chinese Hackers Rebuild Botnet After FBI Takedown, Targeting Critical Infrastructure
Volt Typhoon, a Chinese state-sponsored hacking group, has swiftly reconstructed its malware botnet network following FBI disruption in January 2024. Within 37 days, the group compromised 30% of visible Cisco routers, raising concerns about persistent cyber threats to critical infrastructure.





