Featured
YubiKey Faces Criticism for Selling Devices with Vulnerable Firmware

YubiKey, a leading hardware authentication provider, is under fire for distributing devices with outdated, vulnerable firmware. This shocking revelation affects even high-end FIPS-certified versions, raising concerns about the company's inventory management and commitment to customer security.
The Hidden Danger of Useless Security Controls: Wasting Resources and Undermining Cybersecurity
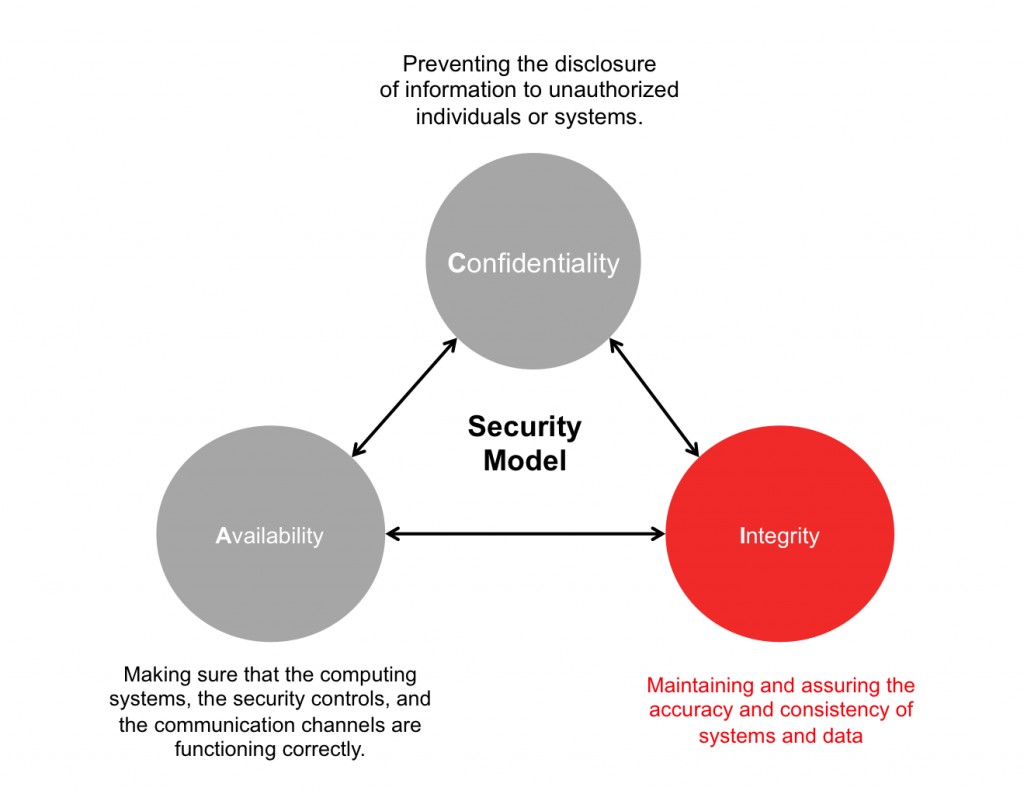
Many organizations implement ineffective security measures that waste resources and potentially make systems less secure. Learn how to identify and eliminate these useless controls to focus on genuine cybersecurity challenges.
AI-Powered Bullfrog: The Future of Drone Defense

The Bullfrog, an AI-driven autonomous machine gun system, revolutionizes aerial defense with unmatched precision against drone threats. Developed by Allen Control Systems, it addresses urgent military needs while raising questions about the future of autonomous weapons.
57 Million Hot Topic Customers Alerted to Data Breach by Have I Been Pwned
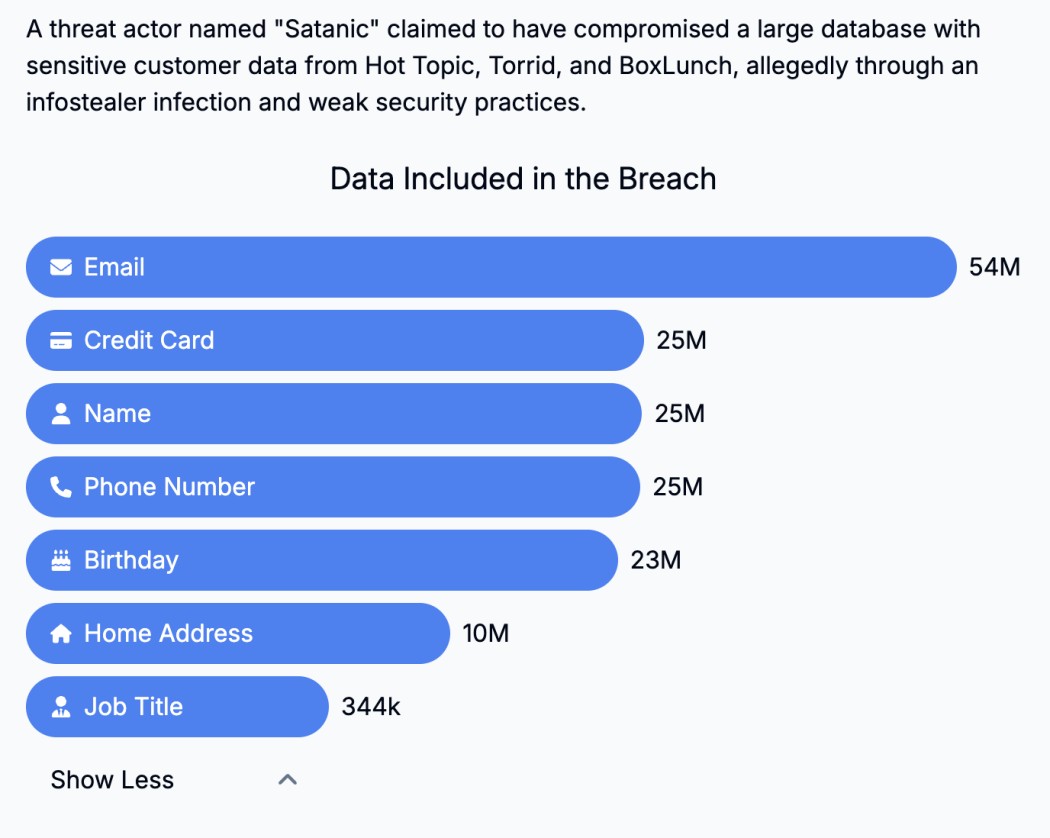
Have I Been Pwned notifies 57 million individuals of a major data breach at Hot Topic, a popular retail chain. Affected customers are urged to take immediate action to protect their personal information.
Amazon Employee Data Exposed in Third-Party Vendor Security Breach

Amazon confirms a data breach affecting employee work contact details due to a security incident at a property management vendor. The company assures that core systems remain secure, while a hacker claims possession of 2.8 million lines of stolen data.
HPE Patches Critical Vulnerabilities in Aruba Access Points

HPE releases urgent security updates for Aruba Networking Access Points, addressing six flaws including two critical bugs. Users are urged to apply patches promptly to protect against potential unauthorized command execution and network attacks.
Critical Flaw in Microsoft Bookings Exposes Users to Account Hijacking and Impersonation
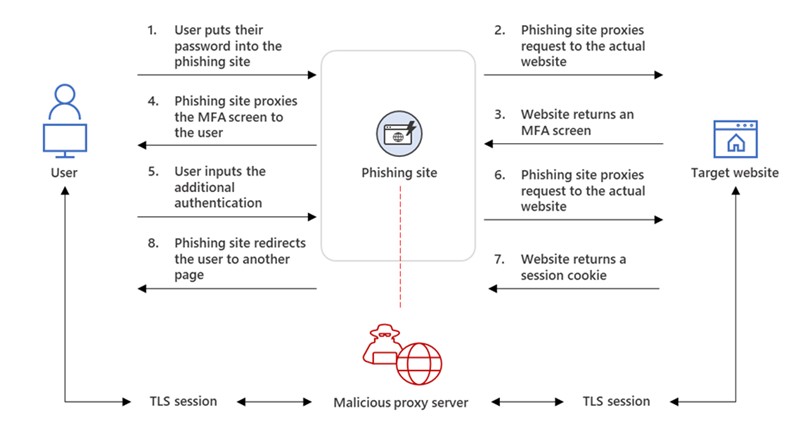
A severe vulnerability in Microsoft Bookings allows unauthorized access and key personnel impersonation, raising cybersecurity concerns. Users are advised to implement additional security measures while Microsoft works on a fix.
Stealthy New Remcos RAT Variant Evades Detection with Fileless Techniques
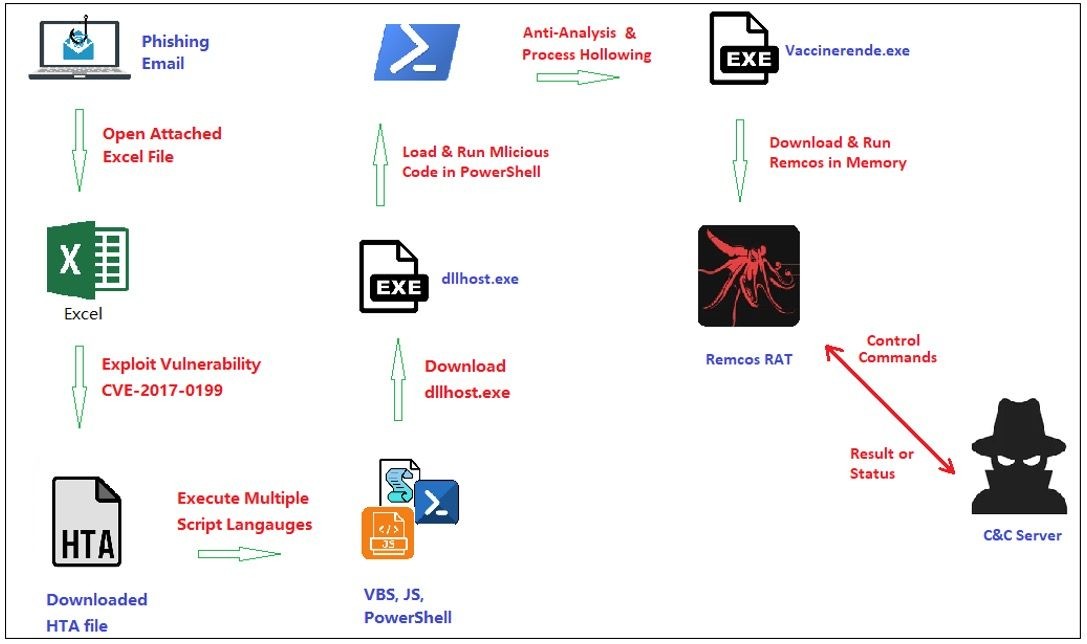
Security researchers uncover a sophisticated new version of the Remcos remote access trojan using advanced evasion methods. This fileless malware variant exploits vulnerabilities and leverages legitimate processes to avoid detection while providing attackers extensive remote control capabilities.
The Rising Threat of AI Deepfakes: Navigating Cybersecurity Challenges in a Synthetic World

AI-powered deepfakes pose significant risks to cybersecurity, enabling sophisticated identity theft and social engineering attacks. As the technology advances, combating these threats requires a multi-faceted approach involving detection algorithms, media authentication, and increased public awareness.